Share this
Advancing Zero Trust with NSA’s Guide & Elisity’s Solutions
by Dana Yanch on Mar 6, 2024 9:33:30 AM
The National Security Agency (NSA) has issued pivotal guidelines to advance cybersecurity through Zero Trust. This model challenges traditional network defenses by promoting the philosophy that no entity inside or outside the network is inherently trustworthy. Instead, verification is required from everyone trying to access resources on the network.
The recently published “Advancing Zero Trust Maturity Throughout the Network and Environment Pillar” marks a significant step in this direction. The guidelines underscore a strategic shift towards granular network control and data protection to combat internal and external threats preemptively.
Read the full document here: Advancing Zero Trust Maturity Throughout the Network and Environment Pillar
NSA Guidelines Overview:
The NSA’s comprehensive framework encompasses seven pillars, with the network and environment pillars as a cornerstone for implementing Zero Trust principles. Among its key recommendations, the document calls for detailed data flow mapping to illuminate potential vulnerabilities and a thorough segmentation of applications and workloads to contain breaches effectively.
Central to these guidelines is the advocacy for robust end-to-end encryption and the adoption of software-defined networking, which provides flexible and secure network configurations crucial for safeguarding data integrity.
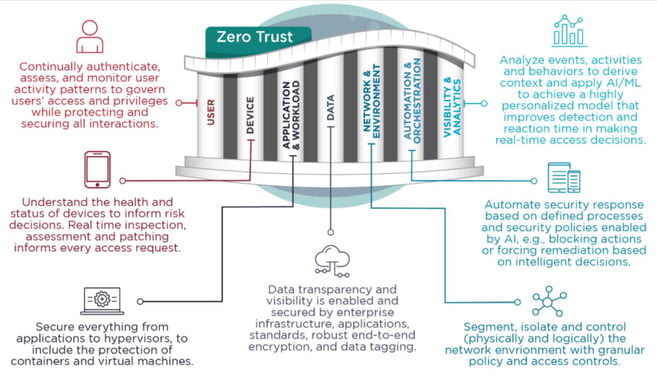
NSA Guidelines Overview:
To solidify cybersecurity, the NSA has published a comprehensive set of recommendations within the Cybersecurity Information Sheet entitled “Advancing Zero Trust Maturity Throughout the Network and Environment Pillar.” This directive serves as a vital component of the Zero Trust (ZT) security model, emphasizing the need to dismantle the traditional paradigm of perimeter-centric security in favor of a more robust, in-depth defensive strategy that addresses both internal and external threats.
Core Pillar Capabilities
The ZT maturity model proposed by the NSA hinges on several key capabilities within the network and environment pillar:
-
Data Flow Mapping: Organizations are instructed to delineate the movement of data across their networks. This mapping exercise illuminates the data journey, revealing potential vulnerabilities, and laying the groundwork for robust data protection and anomaly detection.
-
Macro and Micro Segmentation: The NSA advocates for segmentation at two levels. Macro segmentation delineates broad network areas based on security requirements, while microsegmentation divides these into finer, more controlled segments. This strategy is instrumental in confining network intrusions and mitigating the spread of breaches.
-
Software Defined Networking (SDN): SDN is presented as a pivotal technology for realizing the ZT vision. By enabling centralized control and the automation of network responses, SDN facilitates the dynamic isolation and protection of network resources.
Implementation Focus
The guidance specifies that:
-
Network Access Definitions and Controls: Critical resources should be isolated via definitive network access parameters, and robust controls should be established to manage data flows within the network.
-
Encryption and Visibility: Employing end-to-end encryption ensures the confidentiality and integrity of data, whether at rest or in transit. Additionally, a clear enterprise-wide visibility into network and data flows is essential for detecting anomalies and enforcing security policies.
-
Adaptation to Evolving Threats: As organizations advance their network control, the guidelines stress the significance of enhancing defense-in-depth postures, which helps to limit any network intrusions to a minimal portion of the network.
In totality, these guidelines represent a forward-leaning approach to cybersecurity, where persistent verification, meticulous data control, and the assumption of internal threats constitute the foundation of network and organizational resilience against sophisticated cyberattacks.
Elisity’s Alignment with NSA Guidelines
Elisity's microsegmentation solution is in direct alignment with the NSA’s guidelines for advancing Zero Trust maturity. By deploying Elisity, organizations can effectively meet the NSA’s key recommendations at every maturity level: preparation, basic, intermediate, and advanced.
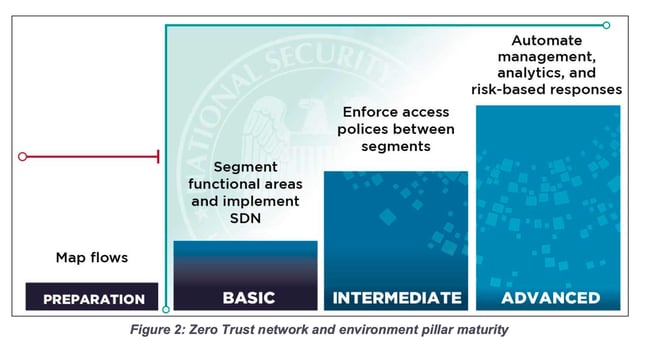
Preparation Phase: Device Integration and Visibility
Elisity’s IdentityGraph™ engine lays the groundwork for Zero Trust by providing complete visibility into every device's activity, security posture, and identity data. This initial step is critical for establishing a Zero Trust environment, as it ensures that all devices—whether trusted workstations or new IoT devices—are seamlessly integrated and managed within the network, setting the stage for detailed policy creation and enforcement.
Basic Level: Policy Distribution and Network Access Control
At the basic level, Elisity facilitates selective distribution of policies to policy enforcement points using its policy groups and policy sets. This is essential for controlling network and data flows in accordance with NSA’s recommendations, thereby defining network access and preventing unauthorized access.
Intermediate Level: Identity-Based Microsegmentation
Elisity’s identity-based microsegmentation provides a sophisticated policy language that utilizes identity and context over traditional indicators like location or IP. This capability supports the NSA’s guidelines for segmenting applications, workloads, and employing encryption. It is particularly applicable in complex network environments like healthcare and manufacturing environments, offering an elevated security measure for sensitive data.
Advanced Level: Integrations with Crowdstrike, Claroty, and Medigate for Dynamic and Risk-Based Policies
At the advanced level, Elisity’s integrations with Crowdstrike, Claroty, and Medigate enable dynamic and risk-based policy enforcement. By leveraging real-time analytics and threat intelligence from these integrations, Elisity's solution can automatically respond to threats, ensuring an advanced protection layer against sophisticated cyber threats.
By addressing each phase of the Zero Trust maturity model, Elisity demonstrates a comprehensive capability to support organizations in implementing NSA’s guidelines, effectively advancing their cybersecurity posture through improved network control and data protection measures.
Empower Your Cybersecurity with Elisity
To truly understand and appreciate the protective capabilities of Elisity in the context of the NSA’s Zero Trust guidance, there's no substitute for seeing it in action. We invite you to request a demo and engage with our security experts who can provide an in-depth consultation tailored to your organization's unique challenges and goals.
Request a personalized Elisity demo today and discover how we can help you align with the NSA guidelines, achieve advanced segmentation, and enhance your cybersecurity posture faster and more efficiently than any other solution on the market. Take the first step towards a transformative cybersecurity strategy with Elisity.
Share this
- April 2024 (2)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)
No Comments Yet
Let us know what you think