Share this
Bracing for Tomorrow's Cyberattacks: Embracing Microsegmentation Today
by Taylor Colwell on Sep 21, 2023 7:27:43 PM

It's getting tough out there. Every week, we hear another story of an organization that has been devastated by a cyberattack. Leveraging new and emerging methods such as "Ransomware-as-a-Service" to exploit fresh vulnerabilities that emerge almost daily, cyber adversaries are becoming increasingly agile and relentless. While it's a sobering reality that not every vulnerability can be preemptively addressed, there is a silver lining.
Limiting the lateral movement within networks through microsegmentation emerges as the most viable strategy to contain these threats. By doing so, even if a vulnerability is exploited, its potential to cause widespread damage is significantly curtailed. Let's dive into why controlling lateral movement is the cornerstone of contemporary cybersecurity and how it serves as the first line of defense in an environment riddled with relentless threats.
The Evolving Cyber Threat Landscape: QakBot and Beyond
The world of cybersecurity has been shaken time and again by a myriad of cyberattacks. From smaller-scale incursions that target individual data sets to widespread ransomware attacks that cripple entire infrastructures, no organization is exempt from the risk.
Take, for instance, the sweeping reach and impact of the notorious Qakbot botnet. A threat that has left its mark on the cybersecurity landscape for well over a decade, Qakbot had infected a staggering 700,000 systems globally. Designed as a banking Trojan initially, its evolution was both rapid and menacing. Qakbot transformed into a gateway for delivering ransomware to compromised devices, leading to an estimated loot of $58 million in ransoms in just under two years.
Such was its pervasive influence that an international operation titled ‘Duck Hunt’ had to be orchestrated to disrupt it. The operation not only took over Qakbot's infrastructure but also involved the distribution of a tool that would automatically purge the malware from infected systems. This proactive move saw a seizure of over $8.6 million in cryptocurrency linked to the botnet's illicit activities.
The tale of Qakbot serves as a stark reminder of the tenacity and adaptability of cyber threats. Despite these monumental efforts, experts like Ricardo Villadiego, Founder and CEO of Lumu, highlight that the code's customizable nature makes it a candidate for repurposing by other threat actors. Such fragmented and re-engineered threats can resurface, requiring organizations to remain perpetually vigilant.
John A. Smith, CEO of the Conversant Group, likens the Qakbot infection mechanism to a zombie apocalypse: each compromised machine joins the malevolent horde, amplifying its numbers and capabilities. Yet, the breach, often through the downloading of malicious attachments, underscores the gaps in IT defenses, emphasizing the criticality of advanced preventative measures.
Moreover, dismantling the Qakbot infrastructure doesn't necessarily signify the endgame. As Dave Ratner, CEO of HYAS, points out, the absence of arrests during the takedown implies that the threat actors could potentially erect new infrastructures shortly.
In essence, while operations like 'Duck Hunt' showcase collaborative efforts to tackle widespread cyber threats, Qakbot's legacy serves as a cautionary tale. It underscores the importance of proactive defenses, continuous monitoring, and the adaptability to handle evolving threats, especially as sophisticated malware like Qakbot often leaves lingering vulnerabilities and footholds in its wake.
However, QakBot is just one of a myriad of threats lurking in the digital shadows. The likes of the Mississippi health system cyberattack, the ransomware assault on Prospect Medical Holdings, or the substantial data breach at San Antonio's CentroMed are potent reminders of the escalating threats organizations face daily. These attacks share a common pattern – once they gain a foothold in a network, they leverage the lack of proper segmentation to spread, exfiltrate data, or cause disruptions.
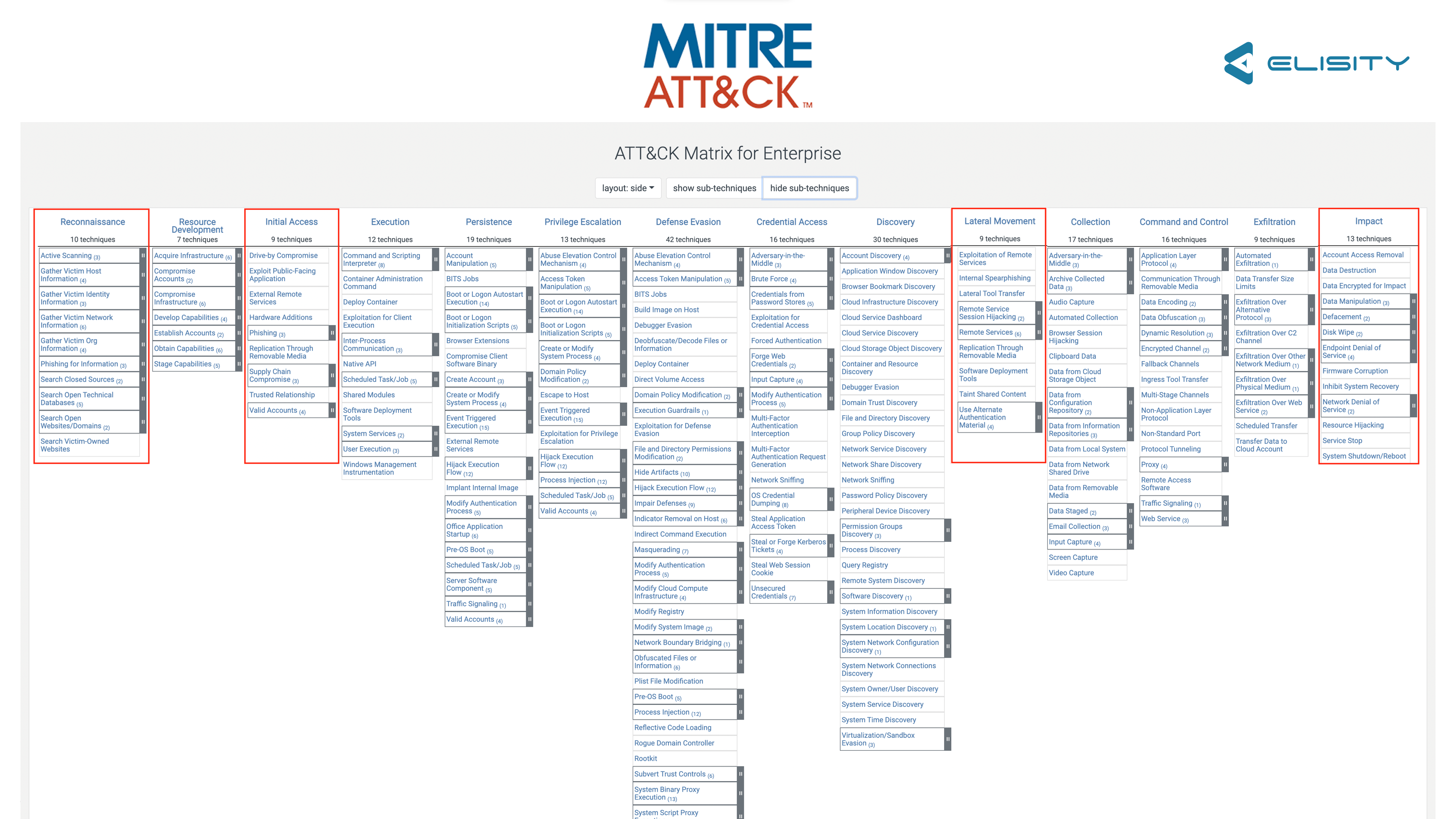
And here's the critical point: cybersecurity standards across the globe recognize this commonality. Instruments like the MITRE ATT&CK Matrix, which provides a comprehensive and detailed understanding of adversary tactics and techniques, consistently emphasize the importance of segmentation. By isolating network segments and ensuring only necessary communication paths are open, organizations can prevent an exploit in one segment from proliferating across the entire enterprise. Furthermore, nearly every compliance standard, be it PCI-DSS for payment data or HHS 405d for healthcare, underscores the pivotal role of segmentation in bolstering an organization's defense mechanisms.
In essence, segmentation isn't just a best practice—it's becoming an industry standard, recommended by experts and mandated by compliance regulations to ensure that even if the outer walls are breached, the castle remains secure.
The Compliance Mandate - Why Leading Standards Recommend Segmentation
As cyber threats evolve, so do the frameworks and regulations designed to bolster organizational resilience against them. Leading compliance standards worldwide have consistently emphasized the significance of network segmentation as a cornerstone of robust cybersecurity. Let’s dive into a few examples:
-
PCI DSS (Payment Card Industry Data Security Standard): Targeted at organizations that handle branded credit cards, PCI DSS explicitly mandates the implementation of a segmented approach. According to Requirement 1.3, organizations must "install and maintain a firewall configuration to protect cardholder data" which includes using a DMZ to limit inbound traffic and not allowing direct public access between external networks and the system components storing cardholder data. Not only that, but the PCI DSS has long issued guidance for using segmentation as a recommended method for protecting cardholder's data. Read the publication here.
-
NIST 800-53 (National Institute of Standards and Technology): Renowned for its comprehensiveness, the NIST 800-53 guidelines for federal organizations and their contractors highlight the need for segmentation in AC-4, SC-7, and SC-32 by advising restricted communications and network partitioning. Many of the NIST subcategories can be met by leveraging the Elisity Platform, and not just segmentation requirements. Check out the illustrations below to see some of the ways Elisity can meet NIST CSF Requirements.
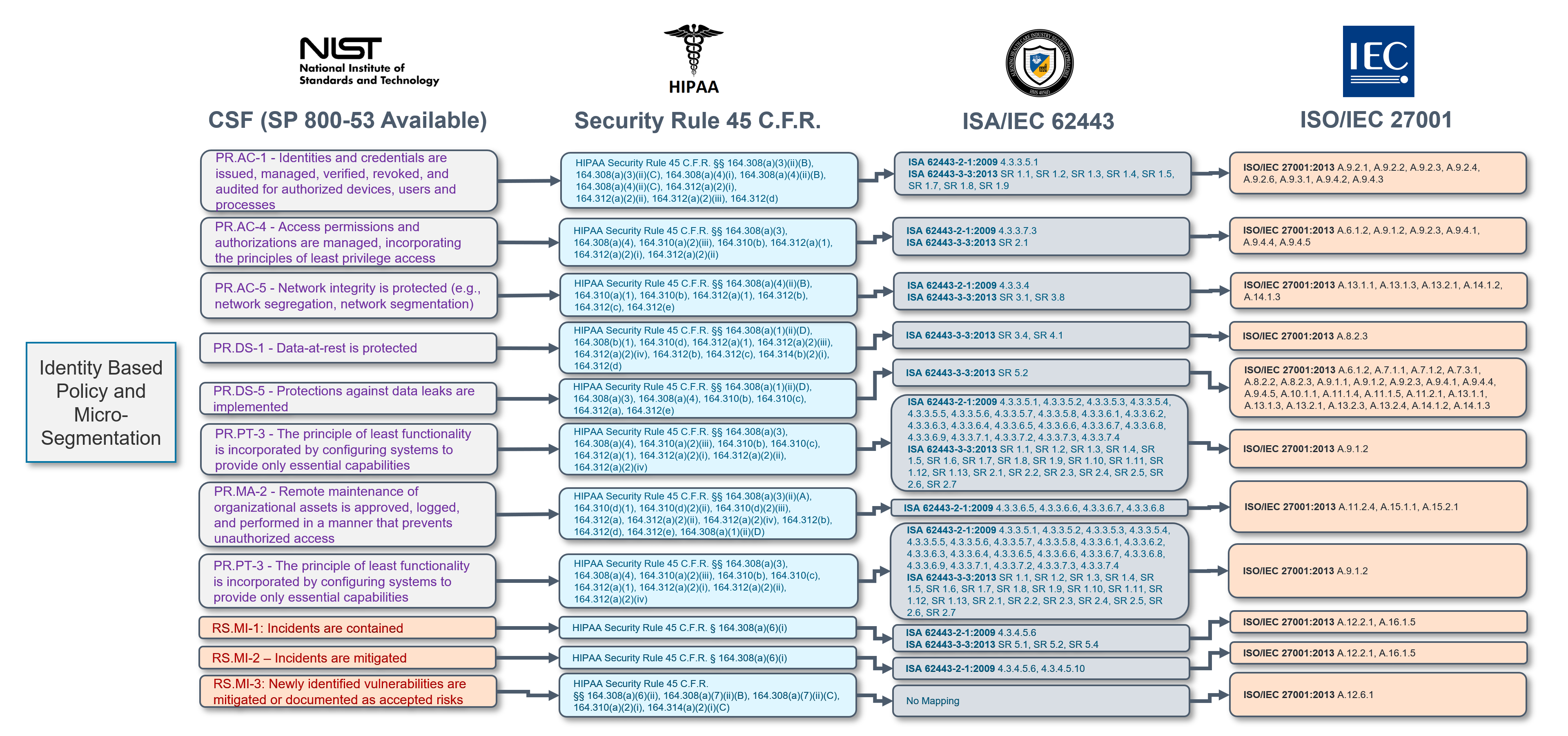
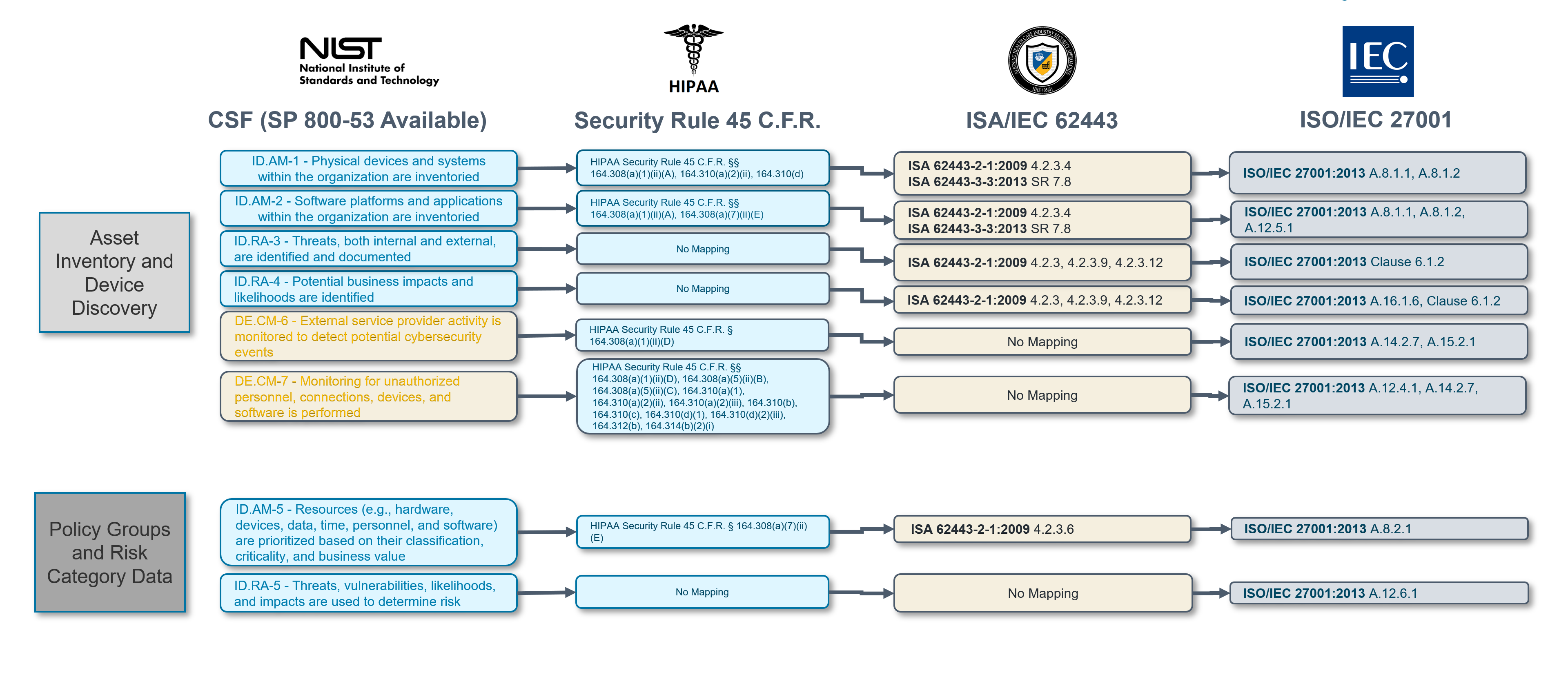
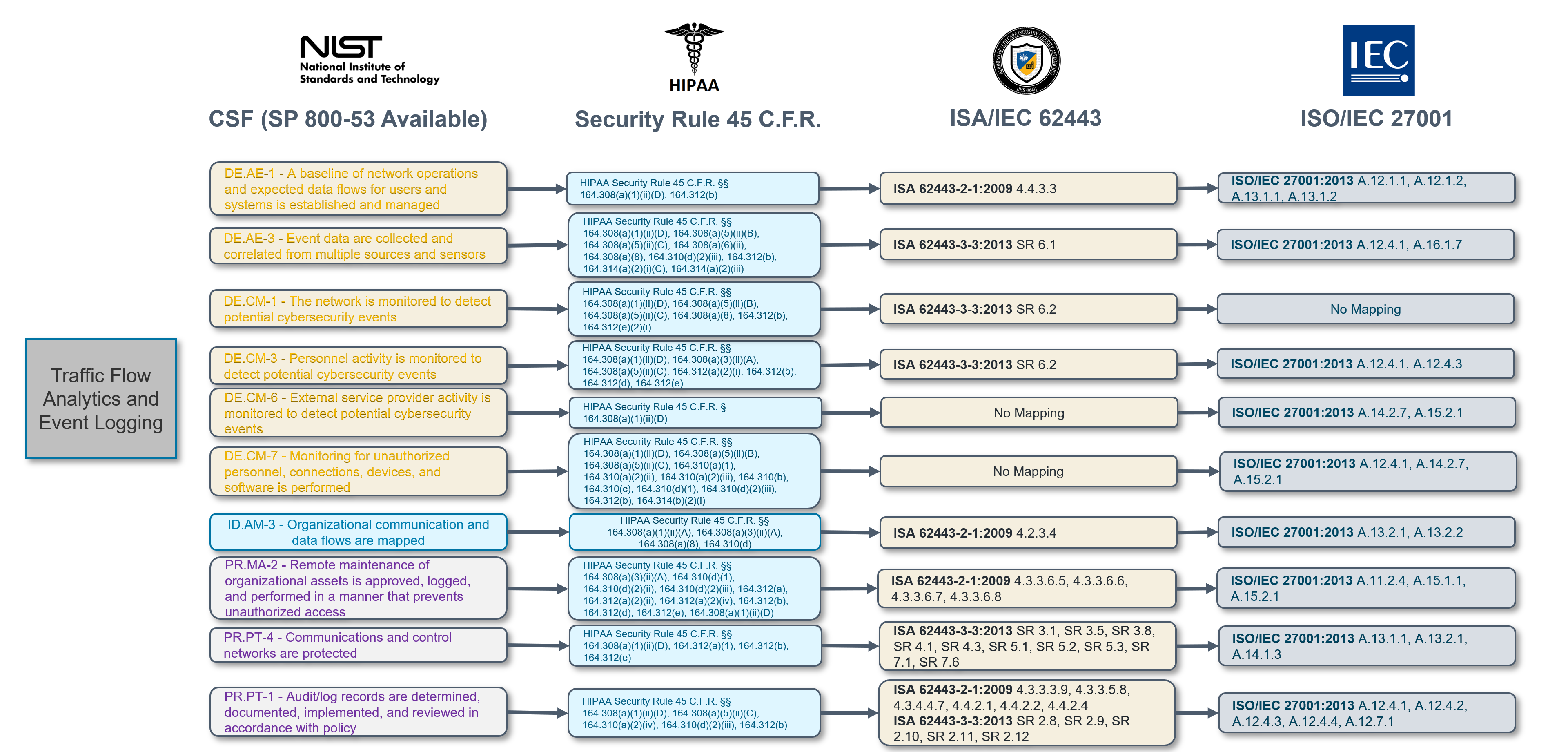
-
ISO/IEC 27001: A globally recognized standard, ISO/IEC 27001 in its A.13.1.3 clause recommends segregating networks based on security requirements. This is indicative of the importance it assigns to effective segmentation in ensuring data security. Check out the illustration below to see some of the ways Elisity can meet ISO/IEC 27001 Requirements.
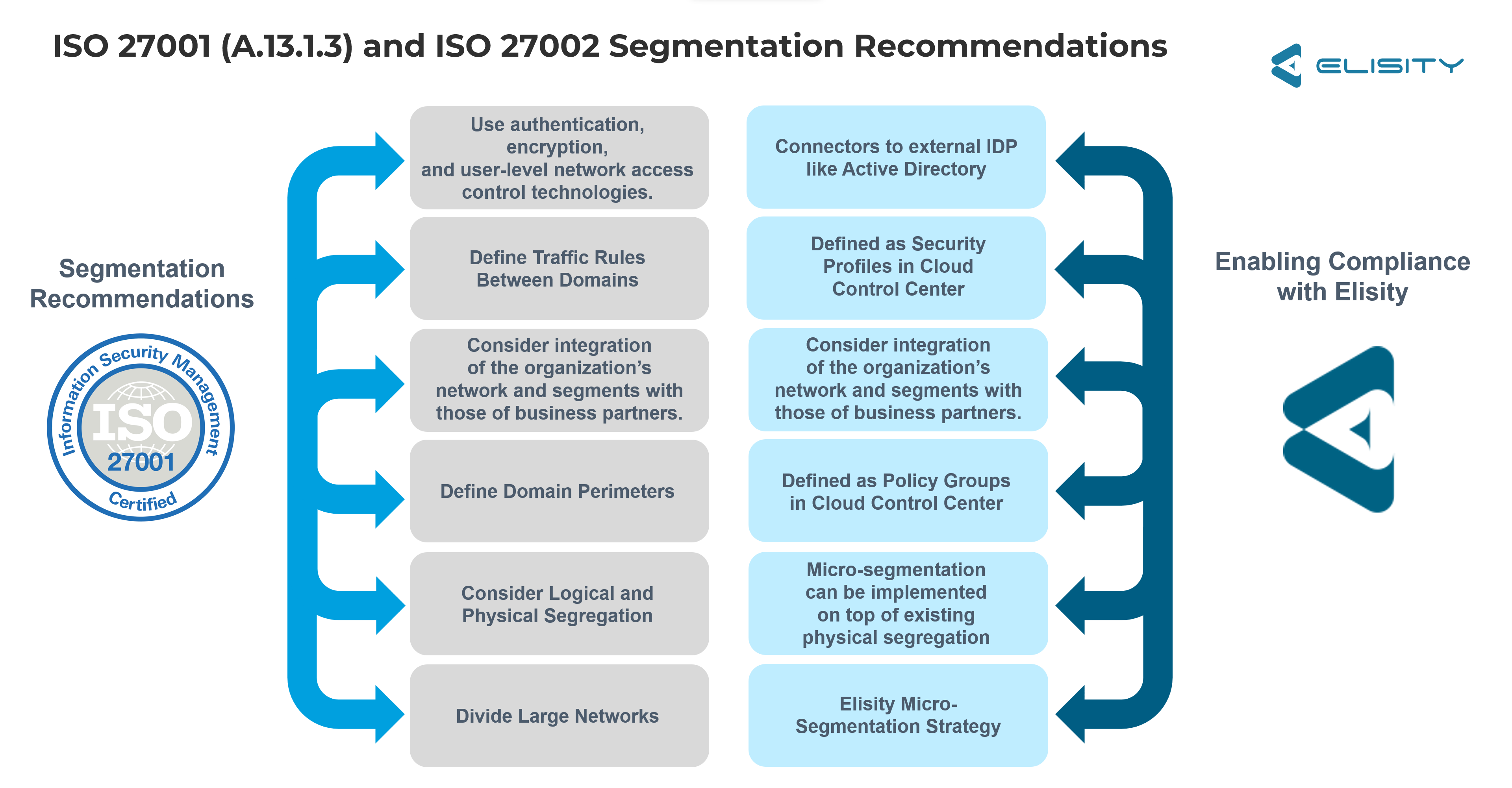
-
HHS 405d (Health Industry Cybersecurity Practices): Specifically tailored for the healthcare industry, HHS 405d provides guidelines to improve cybersecurity practices across various healthcare organizations. Recognizing the critical importance of patient data, the guidelines emphasize the role of network segmentation to limit potential access points for cyberattacks and minimize the potential spread of threats within a network. By isolating critical patient and research data, healthcare providers can safeguard sensitive information from potential breaches. Elisity's platform supports the HHS 405d's emphasis on segmentation, offering healthcare institutions a robust means to align with these best practices.
-
IEC 62443 (Industrial Communication Networks: Network and System Security): Focused on the industrial automation and control systems sectors, IEC 62443 is a series of standards that guide organizations in achieving and maintaining system and network security. Given the critical role of industrial systems in infrastructure and manufacturing, the standards promote network segmentation as a vital aspect of cybersecurity. By segmenting operational technology (OT) networks from IT networks, organizations can reduce the risk of cross-network cyber threats and maintain the integrity of crucial operational systems. Elisity's capabilities align with the segmentation principles of IEC 62443, providing an effective solution for industries seeking compliance with these standards.
-
GDPR (General Data Protection Regulation): While the European Union's GDPR primarily focuses on data protection, its mandates around data integrity and confidentiality indirectly support the notion of network segmentation. By ensuring that only the necessary parts of the network can access specific sets of personal data, organizations can effectively reduce the potential attack surface and improve data protection.
Moreover, the MITRE ATT&CK Matrix, while not a compliance standard per se, is an industry-accepted descriptive model for cyber adversary behavior. It too underscores the significance of microsegmentation. By implementing microsegmentation strategies, organizations can effectively mitigate and manage the lateral movement tactics often described in the matrix, thereby reducing the overall risk. There are four sections of the Matrix that are directly addressed by the Elisity Platform, seen below.
When separate regulatory bodies and industry standards consistently emphasize a strategy, it's a clear indication of its significance. Network segmentation, especially when delivered through solutions like Elisity, isn't just a recommended best practice - it's fast becoming a cybersecurity imperative in a world where threats are continuously on the rise.
Overcoming Traditional Hurtles of Risk Management
Risk is an everyday language that resonates through the corridors of every organization, transcending departments and roles. In today's world, the risks associated with cybersecurity are so intricately woven into the fabric of business operations that they can't simply be siloed off as mere "IT issues." CISOs and cybersecurity professionals are often found trying to navigate a labyrinthine network of compliance regulations, business imperatives, and risk management strategies. This maze only becomes more daunting when the available cybersecurity solutions add layers of complexity, uncertainty, and doubt.
Traditionally, the choice of a cybersecurity solution triggers a host of challenges—will it work as promised? Is it too complex to manage? Will it integrate seamlessly with our existing architecture? The alphabet soup of Firewalls, VLANs, VRFs, NAC, ACLs, and so forth only muddies the water, making stakeholder buy-in more difficult. What we end up with are decisions made out of necessity rather than strategic fit, opting for what seems like the "least bad" alternative. Unfortunately, these traditional solutions rarely offer the agility, ease, or full-scale protection that modern enterprise networks require.
The Elisity Approach: Transforming the Risk Landscape
Elisity transcends these challenges by offering a solution that isn't just another gear in the complex machinery of cybersecurity. Our approach introduces a new paradigm, one that aligns with identity and context over fixed network locations or IP addresses. This shifts the dialogue from one that is fraught with compromise to one of strategic alignment with business objectives and risk management goals.
-
Identity as the Focus: Elisity moves away from the rigidity of IP or location-based controls, focusing on identity and behavior-based policies. This aligns with the ever-changing, dynamic nature of modern businesses. We create a single source of truth for the identity of every asset on your network by graphing together every source of identity data that is available, including integrations with Identity Platforms like ServiceNow, Tenable, Claroty, Medigate, and more.
-
Intelligent Policy Management: Say goodbye to guesswork and blanket policies. Our robust, intelligent policy language enables you to turn traffic analytics into security rules based on actual observed behavior.
-
Seamless Integration and Scalability: Elisity’s platform scales with your needs, ensuring that risk management keeps pace with business growth. Our microservices approach enables auto-scaling and high availability, meaning even the most demanding environments now have a simple, elegant solution.
-
Holistic Risk Management: Elisity provides real-time analytics and insights, allowing for a more dynamic approach to risk management, one that evolves with the threat landscape. You can see a beautiful visulation of what assets are talking to, and using what protocols, in just a few clicks.
-
Unmatched Flexibility: Elisity's deployment model is unlike any other segmentation solution that is available today. We deploy on your existing switching infrastructure, translating easy to understand policies in Cloud Control Center into switch-native constructs at the access layer. This means no more manually modifying lines of rules in the CLI - Elisity automates all of these processes, dynamically modifying necessary configurations throughout your network to allow policies to follow assets accross the entire network edge.
By rethinking how we approach the risk management puzzle, Elisity allows CISOs to turn the tables. Instead of struggling to fit a square peg into a round hole, you can now choose a solution that is designed to fit your unique risk management landscape. In the ever-complicated maze of cybersecurity risk, Elisity serves not just as a guide, but as a pathfinder.
Reimagining Cybersecurity for a Modern World
The ever-evolving cybersecurity landscape demands solutions that aren't just reactive but are proactive, adaptive, and aligned with the dynamic nature of modern enterprises. It's clear that while challenges abound, so do opportunities. Organizations now have the tools at their disposal to reshape the conversation around cybersecurity from one of apprehension to one of strategic alignment, agility, and resilience.
Elisity's identity-based approach to microsegmentation, paired with its flexibility, scalability, and intelligent policy management, presents an innovative answer to today's pressing cybersecurity challenges. By focusing on identities over rigid IPs, intelligently analyzing traffic behavior, and seamlessly integrating with existing architectures, we provide a cybersecurity platform that's built for the future.
Your Next Step Forward
Ready to witness how Elisity can redefine your organization's cybersecurity approach? We invite you to join the vanguard of companies leading the cybersecurity evolution.
Step into the future of cybersecurity with Elisity.
Request a demo today and discover how we can help you transform your enterprise's defense mechanisms, ensuring a secure, scalable, and resilient digital landscape for your organization. Don't just adapt; thrive in this new era with Elisity by your side.
Share this
- April 2024 (4)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)
No Comments Yet
Let us know what you think