Are you concerned about your organization’s cybersecurity posture? With the increasing number of cyber threats, ensuring your systems are secure is crucial. The Cybersecurity and Infrastructure Security Agency (CISA) offers a free service to help organizations identify weaknesses and improve their security posture through its Risk and Vulnerability Assessment (RVA) program.
The RVA program is a one-on-one engagement with stakeholders that combines open-source national threat and vulnerability information with data collected through remote and onsite stakeholder assessment activities. This combined information provides the customer with an actionable risk analysis report containing remediation recommendations prioritized by severity and risk.
The RVA service includes penetration testing to determine susceptibility to an actual attack by using current, real-world tactics, techniques, and procedures. The team performs additional testing and assessments, including network, web application, wireless, war dial, and social engineering in the form of an email phishing campaign. The team also conducts a configuration review of operating system and database settings and configurations to identify security issues.
The objectives of the RVA program are to identify weaknesses through network, system, and application penetration testing, test stakeholders using a standard, repeatable methodology to deliver actionable findings and recommendations, and analyze collected data to identify security trends across all RVA stakeholder environments.
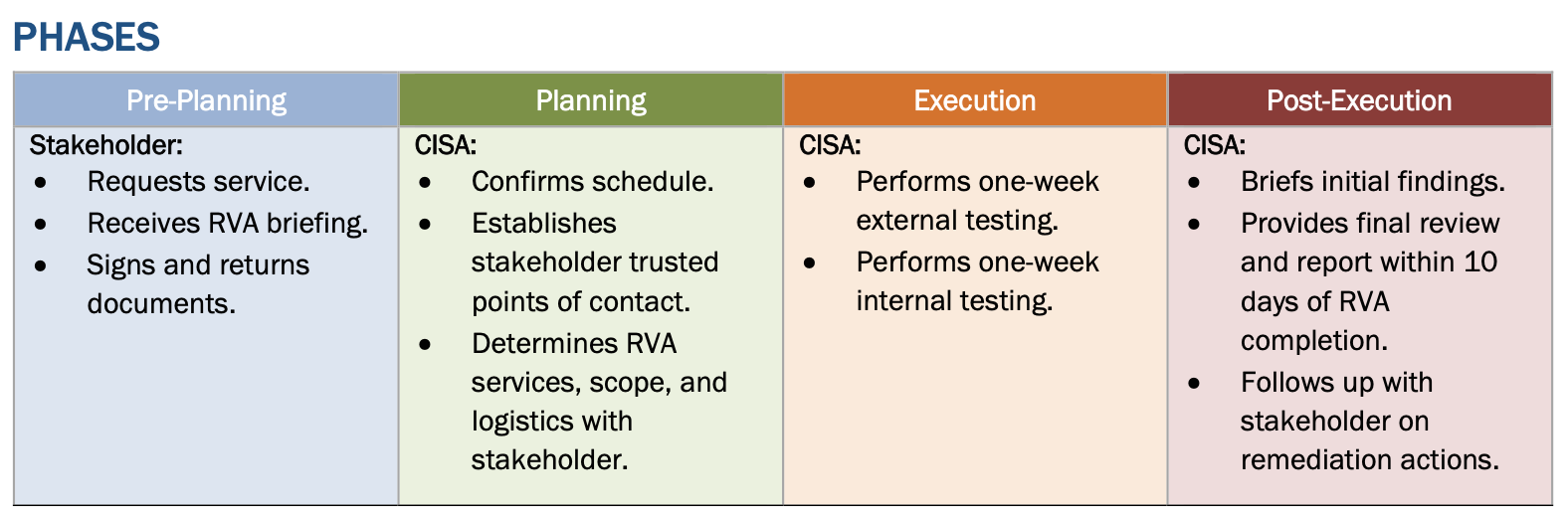
The RVA program has four phases: pre-planning, planning, execution, and post-execution. During the pre-planning phase, the stakeholder requests service receives an RVA briefing, and signs and returns documents. In the planning phase, CISA confirms the schedule, establishes stakeholder trusted points of contact, and determines RVA services, scope, and logistics with the stakeholder. In the execution phase, CISA performs one-week external and internal testing, briefs initial findings, provides a final review and report within ten days of RVA completion, and follows up with the stakeholder on remediation actions. Finally, in the post-execution phase, CISA closes out the RVA.
To get started with the RVA program, organizations can contact vulnerability@cisa.dhs.gov. CISA’s assessments are available to both public and private organizations at no cost. However, service availability is limited, and delivery timelines are available upon request. CISA prioritizes service delivery queues continuously to ensure that no stakeholder/sector receives a disproportionate amount of resources and that the data collected is a diverse representation of the nation.
CISA’s RVA program is an excellent opportunity for organizations to identify weaknesses in their cybersecurity posture and improve their security posture. By using the RVA service, organizations can get actionable findings and recommendations to address security issues. So, use this free service and contact vulnerability@cisa.dhs.gov to get started today!
No Comments Yet
Let us know what you think