Share this
The Case for Leveraging Your Switches as Policy Enforcement Points
by Dana Yanch on Feb 1, 2022 12:02:01 PM
Elisity recently announced the availability of the Elisity Micro Edge to extend the capabilities of the Cognitive Trust™ platform into brownfield switching infrastructure. Deployed as a containerized application on Cisco Catalyst 9300 series switches, or as a virtual machine for Cisco Catalyst 3850 switches, as well as on other vendor platforms, the solution enables organizations to quickly gain visibility into assets and traffic flows at the edge of the network and begin building policies to protect the most critical enterprise assets from malicious network traffic. As a result, the most deployed switches in the world can become a significant component of a zero trust strategy for organizations. But why is this a significant breakthrough?
In this blog, we make the case for identity-based segmentation, explain the different methods available, and list the reasons why using switches as policy enforcement points is a simple and intelligent way to secure users, devices, applications, and data across multiple domains.
Operationalizing Zero Trust
2021 has been as much or more challenging than 2020 for network security teams. The pandemic accelerated the disintegration of the traditional network perimeter, creating a hybrid network environment consisting of shared workspaces on campuses and branches, growing hybrid clouds, a remote or hybrid workforce, and the need to secure access to resources regardless of their location. Alongside this transformation, the growing threat of ransomware, advanced persistent threats, and insider threats, have stretched the network security teams’ resources to the limit. Traditional network security technologies’ ability to predict, prevent, detect and contain breaches don’t cut it in this new landscape. The castle and moat approach to securing assets is obsolete because once the perimeter is breached, attackers can move laterally across the network unhindered and often undetected for more than a year, extracting data along the way before detonating their ransomware payloads and other business-impacting exploits.
As a result of this transformation, during these past two years, the zero trust information security model finally took hold among the network security practitioners and risk management leaders. Although the concept of zero trust architectures has been around for over a decade, it was very tough and expensive to operationalize.
As stated by Forrester: “Zero Trust is an information security model that denies access to applications and data by default. Threat prevention is achieved by only granting access to networks and workloads utilizing policy informed by continuous, contextual, risk-based verification across users and their associated devices. Zero Trust advocates these three core principles: All entities are untrusted by default, least privilege access is enforced, and comprehensive security monitoring is implemented.” - David Holmes, Senior Research Analyst
Thanks to the advent of software-defined networking and cloud-delivered security controls, it is no longer difficult and expensive to operationalize a zero trust architecture. There is a patchwork of legacy tools capable of supporting this model, but challenges persist when retrofitting technologies that were originally developed to support obsolete network security constructs that operate on implicit trust. Furthermore, newer solutions that are purpose-built to support zero trust strategies tend to focus on single use cases, whether it is user VPN replacement for remote access, securing workloads across clouds or in the data center (sometimes with a focus on DevOps), or replacing NAC on campuses with identity-based segmentation. There is no vendor closer to achieving a universal solution that secures access across multiple domains using a ubiquitous identity, analytics, and policy engine other than Elisity (and I challenge you to request a demo if you believe this is just a marketing pitch).
From Elisity’s experience and perspective, the biggest hurdles faced by NetSecOps teams when undertaking the journey to find the right solution to support their zero trust strategy occur when trying to address these needs:
- Visibility and identification of all users, devices, and applications
- Simple policy creation and adaptive enforcement
- Restrict lateral movement at the edge of the network
- Least privilege access for contractors and partners
We address all those needs at Elisity with the development of the Cognitive Trust platform (more about this solution ahead). Still, we just leaped forward in the identity-based segmentation department by launching Micro Edge for Cisco Catalyst switches, which is also extensible to other third-party switches. But before delving into this new component of the Elisity Cognitive Trust architecture and what it means for many organizations, let’s quickly describe the benefits of identity-based segmentation and the three styles that exist today, as defined by Gartner.
The Three Styles of Identity-Based Segmentation
Having granular segmentation restricts the propagation or spread of malware in a network. It also facilitates the isolation and segmentation of infected systems. When this is accompanied by policy automation, it provides improved breach containment and treatment. It is just to say that it acts as compensatory control for the entire network. Identity-based segmentation takes policy enforcement beyond VLAN and subnets to hosts and virtual machines. Workload-level traffic control, inspection and policy enforcement facilitates customized policy creation based on the concept of least privilege, which leads to substantial attack surface reduction. Identity-based segmentation done right acts as a strong internal network defense mechanism.
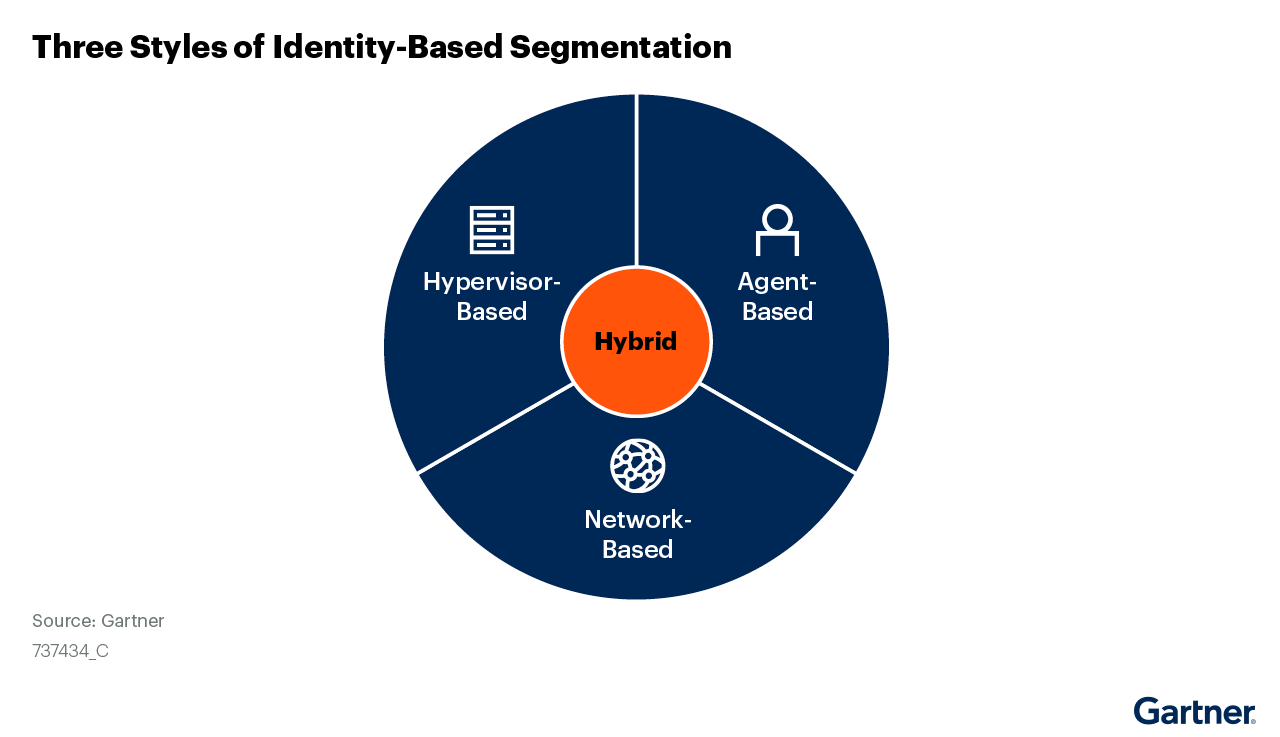
Style 1: Agent-Based
The agent-based solution uses a software agent on endpoint. The endpoint agent monitors and analyzes the traffic that flows in and out of the host to identify appropriate granular policies and to provide application visibility. The large number of collected flows are reduced to a few related flows, on whose basis the policy suggestions are made and presented for validation. The agent-based solutions generally leverage the Windows Filtering Platform (WFP) to enable either the firewall that is built into the OS or the proprietary firewall that is part of the agent software. The WFP filters traffic on OSI Layer 3/Layer 4, and process data collected from WFP is used to make intra-application communication maps and policy decisions.
Style 2: Network-Based
SDN technology virtualizes all network hardware and centralizes its control as a software. It takes the job of traffic management from individual switches and routers to a centralized software that delivers policy-based automation for network devices.
Programmable-fabric-based — Some vendors provide special switches and routers for their network fabric, which can be programmed by highly available controllers. These network controllers publish APIs that enable network programmability.
Network-overlay-based — These solutions make use of network overlays. Overlays are virtual networks layered over physical infrastructure by means of encapsulating Layer 2 traffic over IP.
Style 3: Hypervisor-Based
Some hypervisor vendors offer identity-based segmentation support in their SDN models. Such products abstract the network and security services from hardware and serve them per VM. They embed network and security capabilities in the hypervisor layer, which brings these services very close to the VM operating system (vNIC level). The breadth of coverage forms a strong use case for network-based architectures. It can reach virtualized workloads in the data center or in public clouds, as well as physical servers, IoT, OT and SCADA systems.
Hybrid Architectures
Some vendors offer solutions with multiple architecture models. For instance, the vendors of an SDN-based approach also have agent-based solutions, and vendors of agent-based solutions have provisions for handling systems where agents cannot run. This strategy has been mainly driven by the need of having a uniform solution across hybrid data centers and to overcome the shortcomings of any one form.
Elisity’s Approach to Identity-Based Segmentation
 So what about Elisity? What style of identity-based segmentation do we offer with the Elisity Cognitive Trust platform? Our answer: All of the above; whichever works for the specific environment and use case. Cognitive Trust is Elisity’s cloud-native and cloud-delivered solution for identity-based segmentation of users, applications, and devices, whether managed or unmanaged, across multiple domains. It delivers fast time-to-value by providing real-time visibility into all network assets and data flows to identify high-impact security policies that can then be distributed and enforced as close to the assets as possible. Managed centrally via an intuitive management portal, Cognitive Trust makes zero trust network security easy and accelerates the zero trust journey to reduce the attack surface.
So what about Elisity? What style of identity-based segmentation do we offer with the Elisity Cognitive Trust platform? Our answer: All of the above; whichever works for the specific environment and use case. Cognitive Trust is Elisity’s cloud-native and cloud-delivered solution for identity-based segmentation of users, applications, and devices, whether managed or unmanaged, across multiple domains. It delivers fast time-to-value by providing real-time visibility into all network assets and data flows to identify high-impact security policies that can then be distributed and enforced as close to the assets as possible. Managed centrally via an intuitive management portal, Cognitive Trust makes zero trust network security easy and accelerates the zero trust journey to reduce the attack surface.
Elisity does offer an optional Zero Trust Network Access (ZTNA) component to the solution as a Windows and Mac agent that secures the remote workforce’s access to enterprise resources, effectively replacing user VPN clients. But for the edge computing portion of the architecture, Elisity relies on containerized software and virtual machines on hypervisors, to secure users, devices (including userless IoT and Operational Technology devices), applications, and data, on campuses, branches, data centers, and clouds.
As of January 2022, Elisity is able to turn Cisco Catalyst 9300 series switches, and even Catalyst 3850, into intelligent sensors and policy enforcement points. The Micro Edge software enables you to benefit from simplified network security operations and reduced costs while taking advantage of Cognitive Trust’s powerful prevention, detection, and response capabilities that enhance the cybersecurity posture and minimize the attack surface over time. It is an alternative (or complement, depending on the architectural design) to expensive and complex Network Access Control (NAC) solutions and East-West firewalls. Micro Edge also eliminates the need to install and maintain additional hardware, saving organizations time and resources because it deploys as containerized software on switches or on a hypervisor for those switches that cannot host containers.

Why is this a big deal?
First and foremost, Cisco Catalyst is the most deployed switch in the world, with twenty billion US dollars worth of switches deployed to date. Most organizations run on Cisco switching infrastructure and many have unused Catalyst switches stored and collecting dust somewhere that can now be put to good use. It enables those organizations to make full use of Cisco DNA licensing. In short, it boosts the ROI in Cisco hardware and licensing.
Secondly, Elisity leverages the existing enforcement mechanisms available in existing switches intelligently and extends software-defined perimeter-based (SDP) zero trust to the network layer (it effectively brings SDP to third-party switches). This means that this cloud-delivered identity-based segmentation solution does not require new hardware deployments and network reconfigurations. In fact, Elisity Cognitive Trust couldn’t care less about the underlying network constructs that are in place, because it can be deployed as an overlay or underlay using already deployed hardware. Doing so not only saves time and money and delivers fast time-to-value, but also elegantly brings together a ubiquitous zero trust networking strategy for campuses, branches, and data centers.
Finally, Micro Edge gleans identity and telemetry data from many different sources and continuously verifies it, before locally enforcing policies. These policies are managed and distributed by what we dub the Elisity Cloud Control Center, the management portal that enables continuous monitoring, analytics, alerts, and AI/ML-powered policy recommendations. In short, Micro Edge is essential to deliver a low cost zero trust networking solution:
- It makes more sense of the investment in Cisco switches
- Puts in question any planned investment in NAC and East-West firewalls
- Delivers value quickly by reducing the attack surface via micro-segmentation and responsive policies based on identity, contextual attributes, and behavior.
With this approach, firewall policy drift and never-ending NAC projects can become a thing of the past.
Conclusion
Leveraging brownfield infrastructure to migrate to a zero trust strategy is smart and achieves network security goals faster than retrofitting legacy technology or deploying additional hardware. The architecture proposed by Elisity provides:
- The automatic visibility, identification, and inventory of assets in the network.
- The segmentation at the macro (site), micro (device), nano (flow), and transactional levels.
- Access control via distributed computing at the edge, with centrally-managed policies that are enforced as close to the assets as possible with continuous identity verification and authorization. No need to micro-manage expensive East-West firewalls, NACs, ACLs, VLANs, PVLANs, VRFs, and VPNs anymore.
- IT agility and simplicity, driven by integrations, automation, analytics, and the use of existing networking equipment. A scalable way of securing assets that is simple, cost-effective, scales without network performance trade-offs and delivers value quickly.
With Elisity CognitiveTrust, you can move away from centralized IP/Network-based filters at the firewall and to a distributed identity-based policy fabric at the access layer (closer to the source). Elisity delivers intelligent Zero Trust Access by transforming your existing network security with a cloud-delivered solution that leverages your brownfield infrastructure.
To learn more about Elisity Micro Edge on Cisco Catalyst switches, Read the Technical White Paper or watch the following video where I present this new component of the network security solution.
About Elisity
Elisity offers an identity-driven control plane for corporate networking and remote access without tying customers to a particular network or network security technology. Its Cognitive Trust platform, delivered as a cloud-based service, is deployed as an overlay or underlay on whatever WAN and/or SD-WAN infrastructure an enterprise prefers to protect data, users, devices, and applications in the data center, the cloud, at home, and everywhere.
Share this
- April 2024 (1)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)
No Comments Yet
Let us know what you think