Share this
Elisity Enables Effective ICS Segmentation by Supporting Cisco Catalyst Industrial Edge Series of Switches
by Dana Yanch on Oct 27, 2022 2:23:37 PM
It’s 3 AM, and you get a call from your operations manager of the auto manufacturing plant where you work. 3 AM? It must be something terrible. She sounds frantic. “Listen,” she says, “I don’t know what happened, but the entire body panel manufacturing line is down. We have reports of thousands of out-of-spec parts on the line. We are in trouble. It’s the end of the quarter, and if we don’t resolve this immediately, we will lose millions. All our jobs are at stake here.”
You quickly jump on the remote access server to check the status of critical systems that run the line and notice the data coming back is entirely out of spec, catastrophically out of spec. Access to your engineering workstation with the control interfaces seems locked out, and the reset process is not responding either. The only way now is to go to the plant in person; more time is lost.
As you drive to the plant, you are racking your brain. “How could this have happened? It’s been running great for years, with not a single hiccup! I programmed and tuned that production line logic to perfection.”
You arrive at the plant and spend the next several hours reprogramming the affected components of the manufacturing line and get things back to how they were when you went to bed the night before. During the process, you notice something weird. Some additional workstations are locked out, critical application servers are offline, and necessary logic controllers have been manually adjusted recently. Even though the line is back up and running, the damage is done. Thousands of parts are ruined and unusable.
After a lengthy root cause analysis, it was determined that critical components of the line had indeed been accessed with malicious intent. Interestingly, even though none of the control systems on the line were exposed to the internet, their coding was remotely modified and without the knowledge of anyone at the plant. It was discovered that an internet-connected patch management server with a fully open and trusted communication channel through the firewall to engineering workstations at lower levels was compromised and used as the initial foothold into the network. From there, the attacker loaded reconnaissance software on the engineering workstation, scanned the network and found unpatched and exploitable PLCs, loaded malicious logic code, and ruined all of the active body panels on the line by adjusting the manufacturing specifications. In an attempt to delay recovery, the attacker locked engineering workstations and shut down whatever application servers they could access within the same network. To top it off, since the plant had not deployed an IT/OT asset discovery solution within the network, there was no easy way to know what else could have been exposed to the attack.
So, what did we learn from this scenario?
- There are entirely too many implicitly trusted communication channels between levels of the ICS network
- Without an asset discovery mechanism, identity based access controls or security analytics, threat actors can hide behind trusted components of the ICS network, run reconnaissance tools undetected and wreak havoc on the IT and OT side of an organization.
Let me show you some interesting statistics.
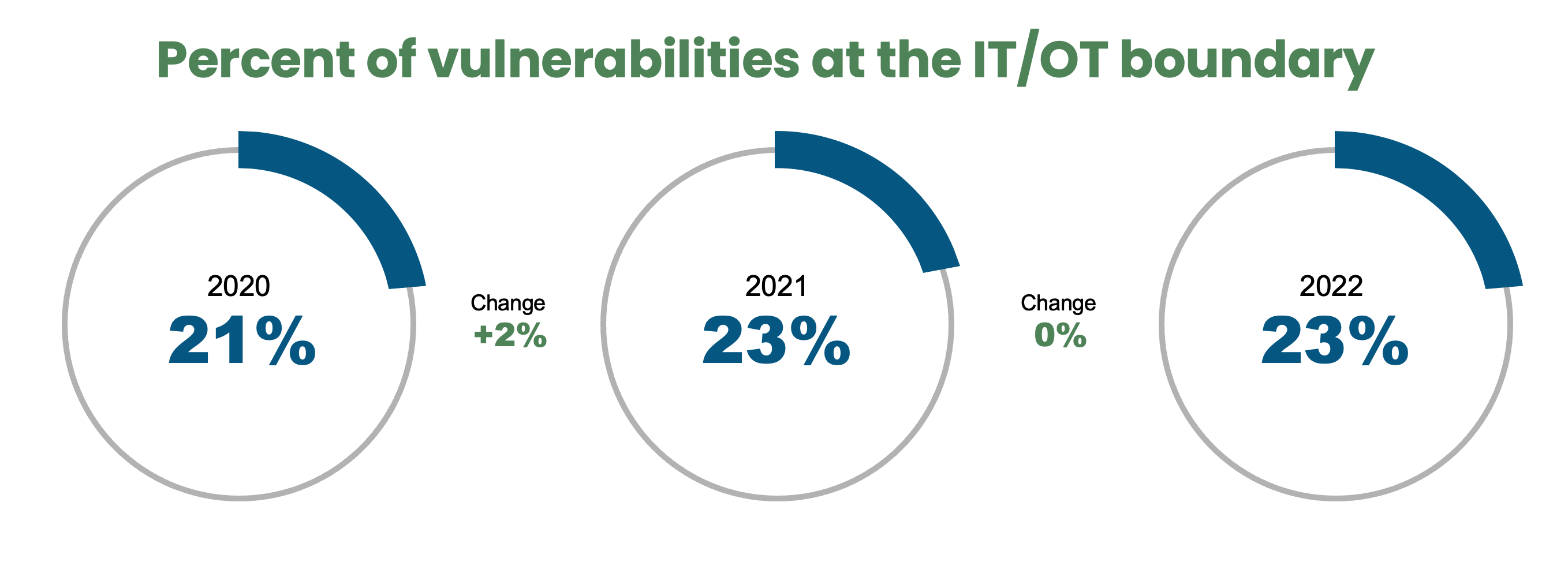
65% of ransomware attacks in the last year targeted manufacturing environments. Currently, 23% of vulnerabilities live at the IT/OT network boundary, and network-exploitable issues accounted for 74% of all advisories in 2019. As we continue to move towards Industry 4.0, the smart factory, connected devices and applications are proliferating, bringing known and unknown vulnerabilities along with them. It goes without saying that your threat landscape is growing rapidly, and these statistics will only worsen. No wonder most, if not all, security compliance standards deem network segmentation as a critical component of your network security posture. The network is the frontline of defense!
Today, Elisity is proud to announce support for the Cisco Catalyst Industrial Edge series of switches.

The Cisco IE switch is a highly capable ICS-focused network access platform and can now be leveraged as a dynamic policy enforcement point as a part of the Elisity identity-based micro-segmentation solution.
Long story short, detecting and profiling IT and OT devices on the network, enabling micro-segmentation policies based on the identity of your ICS devices, users, and applications with zero impact on your operations is possible today! With Elisity you have the capability to stop threat actors at their initial foothold, limiting malicious lateral movement by implementing simple to manage least privilege access policies.
No additional hardware, zero network downtime, and value realized in only days.
I will leave a video here below for you to watch at your convenience to see how effective Elisity’s network segmentation solution truly is and how quickly you can deploy it in your environment.
Reach out to me if you have any questions!
Share this
- April 2024 (2)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)
No Comments Yet
Let us know what you think