Share this
Elisity Releases Version 15.2
by Dana Yanch on Oct 13, 2023 6:43:54 PM
We are thrilled to unveil the latest iteration of Elisity Cloud Control Center, version 15.2. This significant release encapsulates a myriad of new features and optimizations, largely driven by invaluable customer feedback. Our relentless endeavor to enhance user experience and security has fueled this major update, heralding a complete overhaul of our identity engine. The revamped engine now encompasses groundbreaking identity functions, pushing the boundaries of what's possible in cloud management.
IdentityGraph™
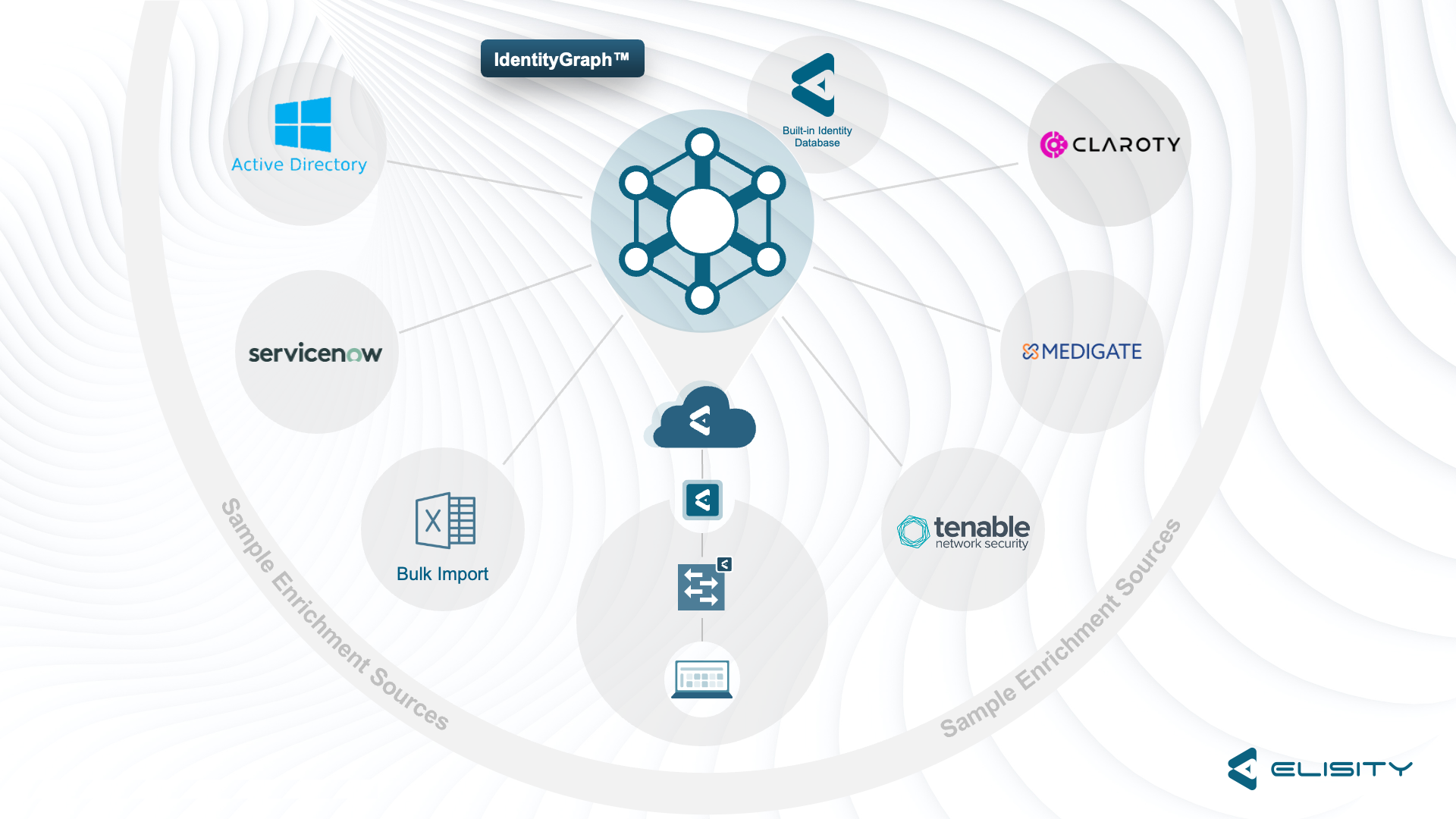
IdentityGraph™, a pivotal enhancement to the Elisity Cloud Control Center, acts as the backbone of our innovative Identity Engine. IdentityGraph™ is not merely a database; it is an intricate mapping service that dynamically constructs a graph, detailing users, devices, and applications along with their identity attributes, traffic patterns, and interrelationships. This feature enables you to harness the data collated and mapped to formulate dynamic, confidence-boosting asset groups and policies, ensuring continuous verification of all entities in your network. Furthermore, IdentityGraph™ doesn’t work in isolation; it seamlessly connects with platforms like Medigate, Claroty, ServiceNow, and Tenable, perpetually enriching data for heightened device attribute accuracy. Visualize traffic to and from known assets effortlessly with the Elisity traffic matrix, providing you with an unparalleled view of your device and users and how they are affected by the policies you build leveraging IdentityGraph™. This is instrumental in crafting effective, least privilege access policies, fortifying your network’s security posture while maintaining a user-friendly interface.
Learn more about IdentityGraph™ here.
Bulk Policy Actions
In the Elisity Cloud Control Center 15.2, Bulk Policy Actions is a feature designed to streamline your policy management process and enhance operational efficiency. With Bulk Policy Actions, you can now select and manipulate multiple policies simultaneously, enabling you to execute functions such as "Activate/Simulate" and "Delete" across numerous policies in a single action. This not only significantly reduces the number of clicks but also minimizes the margin for error, ensuring that your policy management is both efficient and accurate. Whether you are simulating policies for testing or activating them across your network, the new bulk actions feature allows you to manage policies en masse, saving time and ensuring consistency across your environment.
Multi-Select Policy Creation
Introducing Multi-Select Policy Creation, a feature meticulously designed to elevate your policy deployment experience in the Elisity Cloud Control Center. This functionality is engineered to conserve your time and effort by enabling the deployment of a single policy across multiple policy groups simultaneously. Within the Policy Matrix, users can now effortlessly multi-select Policy Group cells and uniformly apply the desired policy to all selected cells. We’ve ensured a user-friendly experience by providing a clear visualization of selected and non-selected cells, along with a straightforward depiction of Policy Group pairings that will utilize the policy for enforcement. Enjoy the flexibility of selection methods: choose entire rows in a single click, select cell groups by clicking and dragging, or utilize the shift key to pinpoint and select specific cells. The Multi-Select Policy Creation feature not only simplifies policy application but also ensures consistent policy enforcement across various groups, enhancing both security and operational efficiency.
Learn more about multi-select here.
Tenable Connector
The Tenable connector, a strategic integration with Tenable Security Center, enhances the Elisity Cloud Control Center’s capability to make informed policy decisions based on precise device classifications. Tenable Security Center, known for its meticulous device identification through passive network traffic information collection, now synergizes with Elisity’s rapid device discovery mechanisms. This integration ensures that your devices are not only discovered promptly but also have the most fitting policies applied judiciously. The Tenable Connector does more than just enrich device attributes in IdentityGraph™; it also serves as a Trust Attribute. This means that the Cloud Control Center can validate a device’s existence in Tenable before trusting it and assigning it to a policy group, adding an additional layer of security verification. Designed with user convenience in mind, this connector, akin to our other integrations, can be effortlessly enabled and activated with just a few clicks, making it a seamless addition to your security management toolkit.
Read more about the Tenable Connector here.
Claroty xDome Connector
Elisity is proud to present the Claroty xDome Connector in the Cloud Control Center 15.2, fortifying our commitment to providing robust and scalable cybersecurity solutions. Claroty xDome, a modular, SaaS-powered industrial cybersecurity platform, excels in asset discovery, management, vulnerability mapping, and threat detection, among other functionalities, across IT, IoT, OT, and IOmT devices. The integration of the xDome connector allows Elisity to enrich device attributes, mapped by IdentityGraph, with additional information sourced from Claroty, including firmware version, serial number, and enhanced model detection. This enrichment facilitates the crafting of more granular or business-driven policies, ensuring your cybersecurity measures are both precise and effective. Moreover, the xDome Connector mirrors the functionality of a Trust Attribute, enabling the Cloud Control Center to authenticate a device’s existence in xDome prior to trusting it and categorizing it into a policy group, thereby enhancing security verification layers. With a setup that takes mere minutes, you can immediately begin enriching the IdentityGraph database, ensuring your policies are as informed and effective as possible.
Read more about the Claroty xDome Connector here.
Medigate Connector Update
In version 15.2, we have made an enhancement to one of our most utilized integrations: the Medigate Connector. While the initial integration was focused on enriching attribute data exclusively for medical devices, we have expanded this functionality to encompass all device types, including IT, IoT, and OT, in the latest update. Now, users can achieve the same level of attribute granularity previously exclusive to medical devices for all device categories through Medigate. This enhancement not only broadens the scope of device attribute enrichment but also ensures that your policies across all device types are informed by detailed, accurate data. Whether you’re managing IT infrastructure, IoT devices, or operational technology, the updated Medigate Connector ensures your IdentityGraph is populated with the most detailed and accurate device attributes, facilitating more informed, granular, and effective policy creation and enforcement across your entire digital environment. Moreover, the updated Medigate Connector mirrors the functionality of a Trust Attribute, enabling the Cloud Control Center to authenticate a device’s existence in Medigate prior to trusting it and categorizing it into a policy group, thereby enhancing security verification layers.
Read more about the Medigate Connector here.
ServiceNow Connector Update
In the Elisity Cloud Control Center 15.2, we are excited to introduce an enhancement to our ServiceNow integration, enabling you to utilize ServiceNow CMDB attributes as match criteria when constructing a policy group. While our ServiceNow integration has always served as a Trust Attribute, akin to our other identity integrations, this update allows you to leverage specific CMDB attributes, such as Asset Owner, Asset Tag, Location, Managed by, and more, as match criteria that must be satisfied before a device can be classified into a policy group. This means that the policies you create can be even more targeted and specific, ensuring that devices are classified based on detailed, accurate data and that policies are applied with the utmost precision. By utilizing ServiceNow CMDB attributes in this way, you ensure that your policy groups are not only robust and secure but also tailored to the specific needs and characteristics of your devices, enhancing both security and operational efficiency.
Read more about the ServiceNow Connector here.
Device Labels
Introducing Device Labels, a new feature in the Elisity Cloud Control Center designed to provide a powerful and flexible tool for differentiating devices in your environment, especially when they appear identical or very similar across various sites or environments. These labels are fully user-definable, enabling you to assign unique identifiers based on any parameter that suits your needs, such as location name, manufacturing line name, device owner, zone name, or any custom string of text. Not tied to any specific type of device or network attribute, Device Labels are fully customizable and are designed to provide an additional mechanism to distinctly identify a device or a set of devices. Particularly in environments housing multiple identical devices, Device Labels prove to be invaluable. By matching these identifying attributes in a policy group, users can segregate devices into distinct policy groups, each governed by its unique set of policies, ensuring precise policy application and enhanced network organization and security.
Read more about Device Labels here.
Active Directory Agent Update
The Active Directory (AD) Agent in the Elisity Cloud Control Center 15.2 has been updated, focusing on enhanced functionality and improved performance. The process of re-syncing the connector has been streamlined and is now executed exclusively via the Cloud Control Center UI, making the operation simpler and faster. Furthermore, the role of the Active Directory agent has been refined: it is now utilized solely for device attribute enrichment and trust attribute functionality. This marks a shift from previous versions where it was employed to import AD registered devices into the Cloud Control Center. This update not only simplifies the management of your AD integration but also optimizes the performance and reliability of the AD agent, ensuring that your device attributes are enriched accurately and efficiently, and that your trust attributes function with the utmost reliability.
Learn more about the Active Directory Agent Update here.
Active Directory Match Criteria Update
Elisity Cloud Control Center 15.2 brings you an enriched Active Directory (AD) Match Criteria update, expanding the array of AD attributes that can be utilized when defining the match criteria for a Policy Group. Now, administrators can leverage additional device attributes such as Device Account ID, Device Account Name, and Device Member Of, enhancing the specificity and accuracy of policy group matching. Moreover, a wealth of User match criteria has been introduced, including User Account ID, User Account Name, User Company, User Department, User Title, and more, providing a more granular and tailored approach to policy application based on user attributes. This enhancement allows for more precise policy group creation and enforcement, ensuring that your policies are as targeted and effective as possible, thereby enhancing both network security and operational efficiency.
Share this
- April 2024 (2)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)
No Comments Yet
Let us know what you think