Share this
From Vulnerable to Vigilant: Addressing the Top 10 Network Misconfigurations with Elisity
by Taylor Colwell on Nov 6, 2023 9:09:29 PM
Today we are going to talk about some of the most common network vulnerabilities that can be found in nearly every network: misconfigurations. Even the most disciplined network security professionals have been guilty of at least one of these configuration mistakes - after all, we are all human. However, leaving these misconfigurations open to exploitation through the lack of proper segmentation is an easy way to find your network compromised by an attacker. Many companies have found themselves in this situation, and the worst part is, the solution is simple.
Overview of the Top 10 Misconfigurations
Recently, the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) Hunt and Incident Response teams have identified the top 10 most observed network misconfigurations during their Red Team and Blue Team assessments. These range from default configurations of software and applications to unrestricted code execution; each contributing significantly to overall system vulnerabilities.
Here is the complete list:
1. Default configurations of software and applications
2. Improper separation of user/administrator privilege
3. Insufficient internal network monitoring
4. Lack of network segmentation
5. Poor patch management
6. Bypass of system access controls
7. Weak or misconfigured multifactor authentication
(MFA) methods
8. Insufficient access control lists (ACLs) on network shares and services
9. Poor credential hygiene
10. Unrestricted code execution
As we explore each of these misconfigurations, we'll also focus on understanding how Elisity, an innovative player in cybersecurity and microsegmentation solutions, can help address these issues. Elisity's unique identity and context-based approach towards enterprise security provide both direct and indirect solutions to these common misconfigurations. By arming ourselves with this knowledge, we can better fortify our systems against potential breaches, and keep a step ahead of the ever-evolving landscape of cyber threats.
Red Team, Blue Team: An Overview
Here is a quick overview for those of you unfamiliar with the Red Team, Blue Team method. The Red Team, analogous to ethical hackers, simulates real-world attacks to test the resilience of an organization's security landscape. On the other hand, the Blue Team is the defending side, responsible for strengthening and maintaining the organization's security posture. Their constant competition allows for identification and rectification of potential vulnerabilities, in this case, network misconfigurations, critical for maintaining a strong security framework.
The NSA and CISA, two highly instrumental governmental organizations in the world of cybersecurity, regularly conduct Hunt and Incident Response assessments using this method. NSA, known for its cryptographic and signals intelligence, along with CISA, the national risk advisor providing comprehensive cybersecurity and infrastructure security, work together to safeguard the public and private sectors' information systems. These assessments lead to revealing the top 10 most observed network misconfigurations. Given their extensive expertise and the critical nature of their work, these findings provide invaluable insights for organizations aiming to bolster their cybersecurity.
It is essential to address these commonly observed misconfigurations as they offer a gateway for security breaches, including unauthorized access, data leakage, and system damages, to name a few. By understanding and resolving these misconfigurations, organizations can significantly enhance their security posture, better protect their critical data, and prevent costly disruptions.
Addressing Default Configurations with Elisity
Default configurations of software and applications represent a significant loophole in cybersecurity. They typically involve pre-set passwords and security settings, which can be easily exploited by malicious actors. For most of these, a five-second google search is all it takes to find the default credentials or configuration you need to exploit these vulnerabilities.
Elisity offers an indirect but effective way to mitigate the risks associated with default configurations. Rather than trying to manually manage and change these configurations, which is often unrealistic, Elisity restricts access to vulnerable devices. By leveraging identity and behavior-based microsegmentation, Elisity successfully limits who can gain access to certain applications and software. This fundamentally reduces the attack surface at the get-go, making it significantly harder for potential threats to exploit default configurations. This roundabout but potent strategy underscores Elisity's innovative approach towards cybersecurity, giving organizations an upper hand in safeguarding their networks.
Ensuring Proper User/Administrator Privilege with Elisity
The second major finding from the Red Team/Blue Team assessments concerns the improper separation of user and administrator privileges. With inadequate separation, users can unintentionally receive administrative powers, leading to untintended changes or creating opportunities for malicious actors. From the Red Team’s perspective, these oversight invite potential attacks, while the Blue Team grapples with the task of ensuring appropriate privilege distribution to avoid security breaches.
Herein lies the benefit of Elisity’s identity-based approach to security. Rather than assigning permissions loosely or broadly, Elisity works to allocate privileges based on the user’s identity, following stringent protocols to verify authorized users. One of Elisity's key strategies includes leveraging Active Directory (AD) groups. By classifying users through specific AD groups, Elisity can selectively allow or deny access to assets, ensuring only those with necessary privileges can gain access. Not only can policies be tailored based on group membership, but they can also utilize titles, departments, locations, and virtually any other AD attribute to fine-tune access controls. This approach doesn’t just provide tight control over who has access to sensitive data and systems, but more importantly, it delivers granular visibility and precise management of user privileges. Consequently, this drastically reduces the risk of privilege misuse or abusive admin activities, strengthening the overall security of the network.
Improving Internal Network Monitoring with Elisity
Another crucial finding from the Red and Blue teams' assessments is the lack of sufficient internal network monitoring. This shortfall leaves gaps in an organization’s security, providing ample room for the Red Team to exploit unnoticed vulnerabilities. On the other hand, the Blue Team endeavors to enhance monitoring capabilities to proactively identify and mitigate these vulnerabilities.
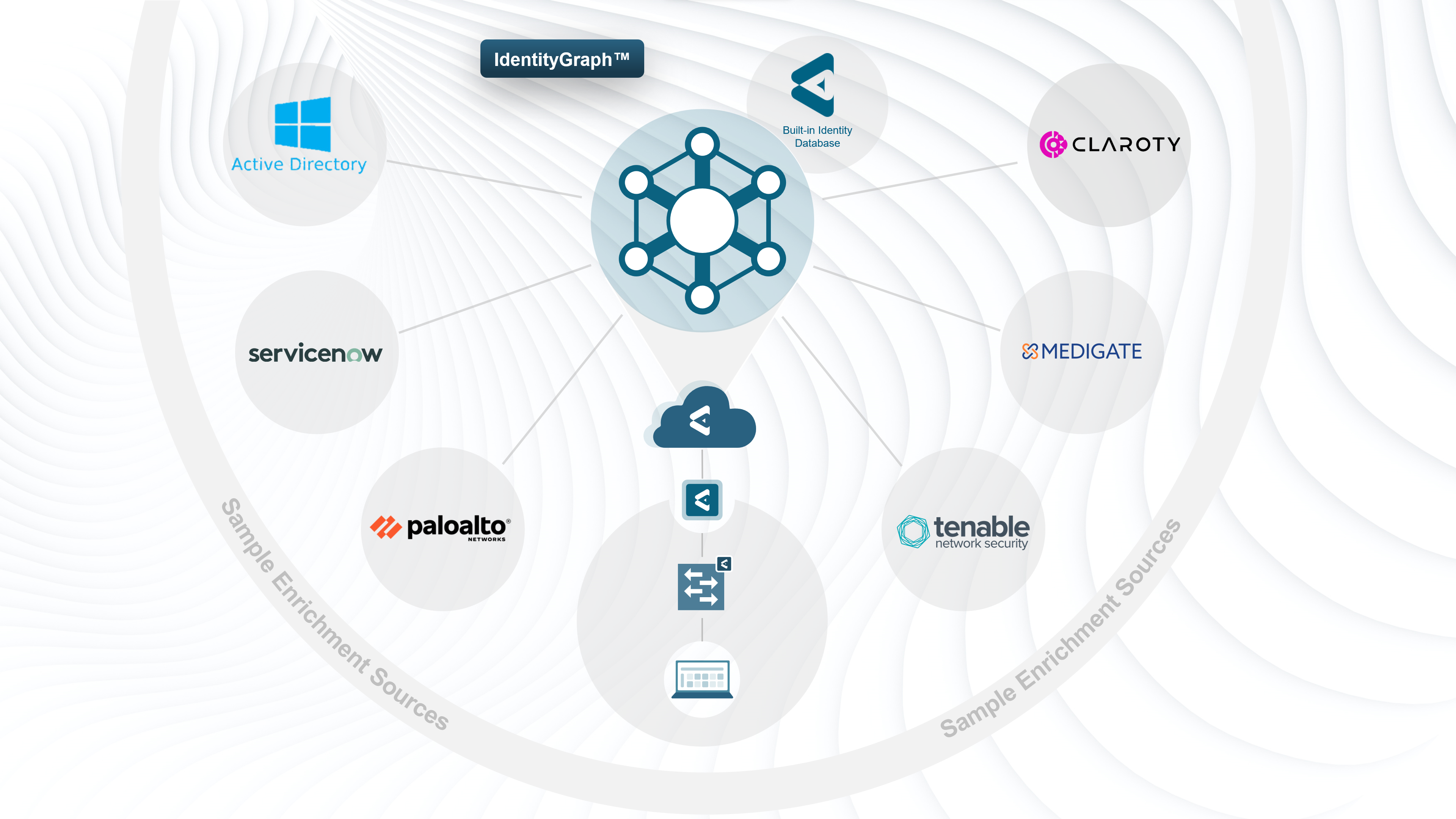
To tackle this issue, Elisity's approach to internal network monitoring is rooted in providing comprehensive asset visibility. IdentityGraph provides a clear and holistic view of the relationships and interactions between different users, devices, applications, and network flows within an organization. This allows the Blue Team to monitor and understand complex dependencies, ensuring unseen threats do not slip through the cracks.
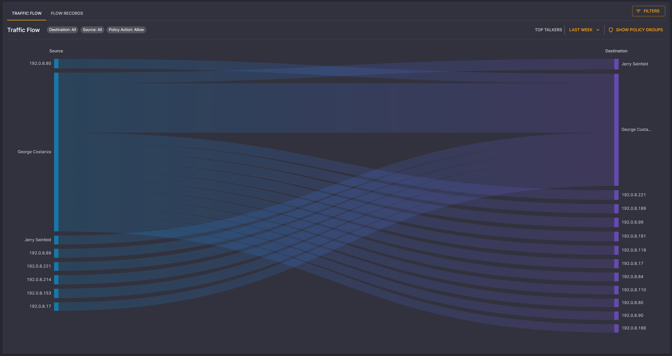
Elisity also allows you to view traffic flows on the network in a convenient matrix view that shows the source group, destination group, and exactly what traffic has been observed, through the Traffic Flow View of the Policy Matrix. This maps out patterns of network traffic in real-time, giving visibility and in-depth analytics of every process on your network. This aids in identifying anomalous network behaviors that may signify potential security breaches, enabling quicker and more informed response. Of course, you can view traffic flows in a more traditional table view, and apply robust filters to find exactly the network traffic you are interested in.
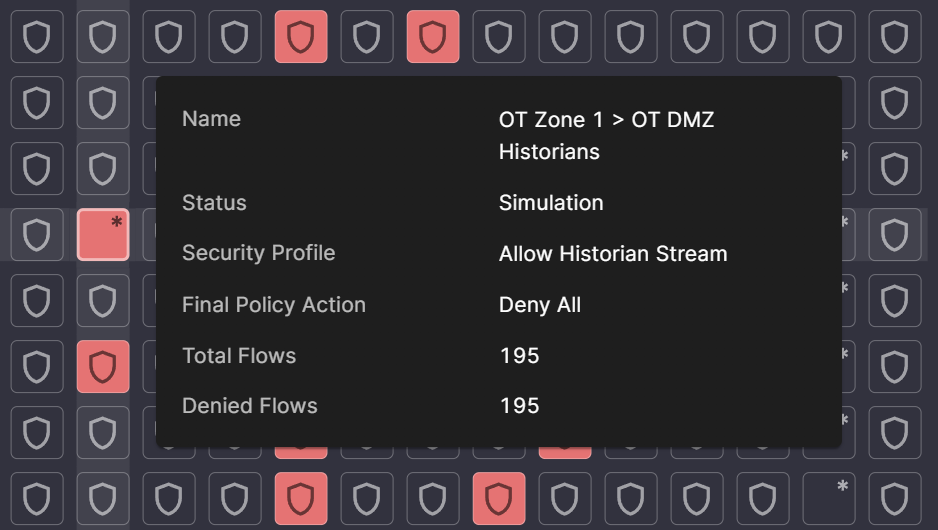
Simulation Mode is a another unique tool that allows the Blue Team to model and predict the impacts of potential security changes before they are implemented. This feature simulates various scenarios, helping identify potential vulnerabilities and allowing teams to course-correct before a risk becomes a reality. You can simulate restrictive policies that use the principles of Least Privilege Access to safely implement policies that would block malicious activity, without the risk of blocking necessary protocols. When you're ready, you can activate the policy with confidence.
Together, these components create a robust monitoring system that gives organizations a deeper understanding of their network’s health and security posture. This comprehensive approach to improving internal network monitoring is a testament to Elisity's commitment to equipping organizations with robust defenses against potential security breaches.
Controlling System Access: Elisity’s Solutions
Among the most striking findings from the NSA and CISA Hunt and Incident Response teams' assessments is the prevalence of system access control bypasses. This vulnerability is a prime target for Red Teams, providing them opportunities to take control of privileged systems. On the flip side, the Blue Team's key defensive strategy encompasses creating robust access control mechanisms to keep potential intruders at bay.
Addressing this issue head-on, Elisity's solution directly and powerfully rectifies this flaw. It enables organizations to exert granular control over their users and assets with its identity and behavior-based access controls. By defining access permissions based on user identity and expected behavior, Elisity ensures that systems are accessible only to authorized individuals carrying out expected roles - minimizing unauthorized access and potential system breaches.
Additionally, Elisity fortifies its access control measures through IdentityGraph and the Policy Matrix. The former provides an accurate and thorough understanding of all the identity data for every asset, while the latter allows the implementation of precise control strategies. With microsegmentation, Elisity can isolate individual workloads, effectively reducing the attack surface and inhibiting lateral movement in the event of a breach.
In essence, Elisity directly nails down system access control bypasses. By providing tighter and more effective access control, Elisity not only drastically reduces the window of opportunity for system attacks but also empowers the Blue Team to maintain a strong defense front.
Patch Management: Making It Effective with Elisity
Poor patch management is another major vulnerability uncovered in Red and Blue team assessments. Out-of-date software and systems often riddle an organization's network, offering the Red Team a buffet of opportunities for exploitation. The Blue Team, meanwhile, grapples with the problem of managing necessary updates to shore up these vulnerabilities.
While Elisity does not provide direct patch management, its solution comes into play for devices that, for various reasons, cannot be patched effectively. Herein is where Elisity's strength shines - by virtue of creating highly restrictive access control policies, it effectively shrinks the attack surface, preventing unpatched devices from being exploited.
By employing identity-based microsegmentation, Elisity quarantines unpatched or vulnerable systems, separating them from the rest of the network. This is a common stragegy that our customers employ: grouping legacy devices with higher vulnerabilities into Policy Groups. You can even leverage integrations with vulnerability tools like Tenable to group assets based on risk scores. This ensures that even if a breach does occurs in an unpatched system, the impact is localized and doesn't spread to other components of the network.
Strengthening System Access Controls with Elisity
The next key problem identified by the NSA and CISA assessments is the insufficiency of access control lists (ACLs) on network shares and services. The Red Team often exploits inadequate ACLs to gain unauthorised access to sensitive network zones, while the Blue Team tries to strengthen ACLs and prevent unauthorised access.
Elisity provides a powerful solution to tackle this common network misconfiguration. It not only assists organizations in managing and enforcing robust ACLs but also offers a paradigm shift from conventional ACL methods to a more granular, context-aware, and dynamic approach towards defining access rules. By going a step beyond traditional IP-based ACLs, Elisity leverages its identity and context-based access control mechanisms to ensure access privileges are granted or denied based on the user’s identity and context at any given moment.
Moreover, Elisity's microsegmentation capabilities create isolated and secure zones within the network, significantly reducing the risk of illicit inter-zone traffic or lateral movement even if an attacker manages to penetrate the initial network perimeter. Tight control over what users and devices can access within the network translates to stronger system access controls and enhanced overall security.
By interweaving the capabilities of identity-based access control with defined ACLs, Elisity provides a secure solution to strengthen system access control and mitigate risks. In this way, Elisity empowers the Blue Team and gives them more control over their defenses against Red Team attacks.
Managing MFA Methods and ACL Management with Elisity
Weak or misconfigured multifactor authentication (MFA) methods, along with insufficient ACLs on network shares and services, are key findings by the Red and Blue Teams. An insecure or inadequately implemented MFA or ACL can present opportunities for unauthorized access to an organization's network, making it a serious concern for the Blue Team.
While Elisity does not directly employ traditional ACLs or directly manage MFA methods, the solution it offers goes far beyond these traditional measures. Instead of the conventional IP-based ACLs typically found in firewalls, Elisity takes a more user-centric, context-aware approach. It defines access rules based on an individual's identity, their roles and their behaviour norms, adding a dimension of dynamic intelligence.
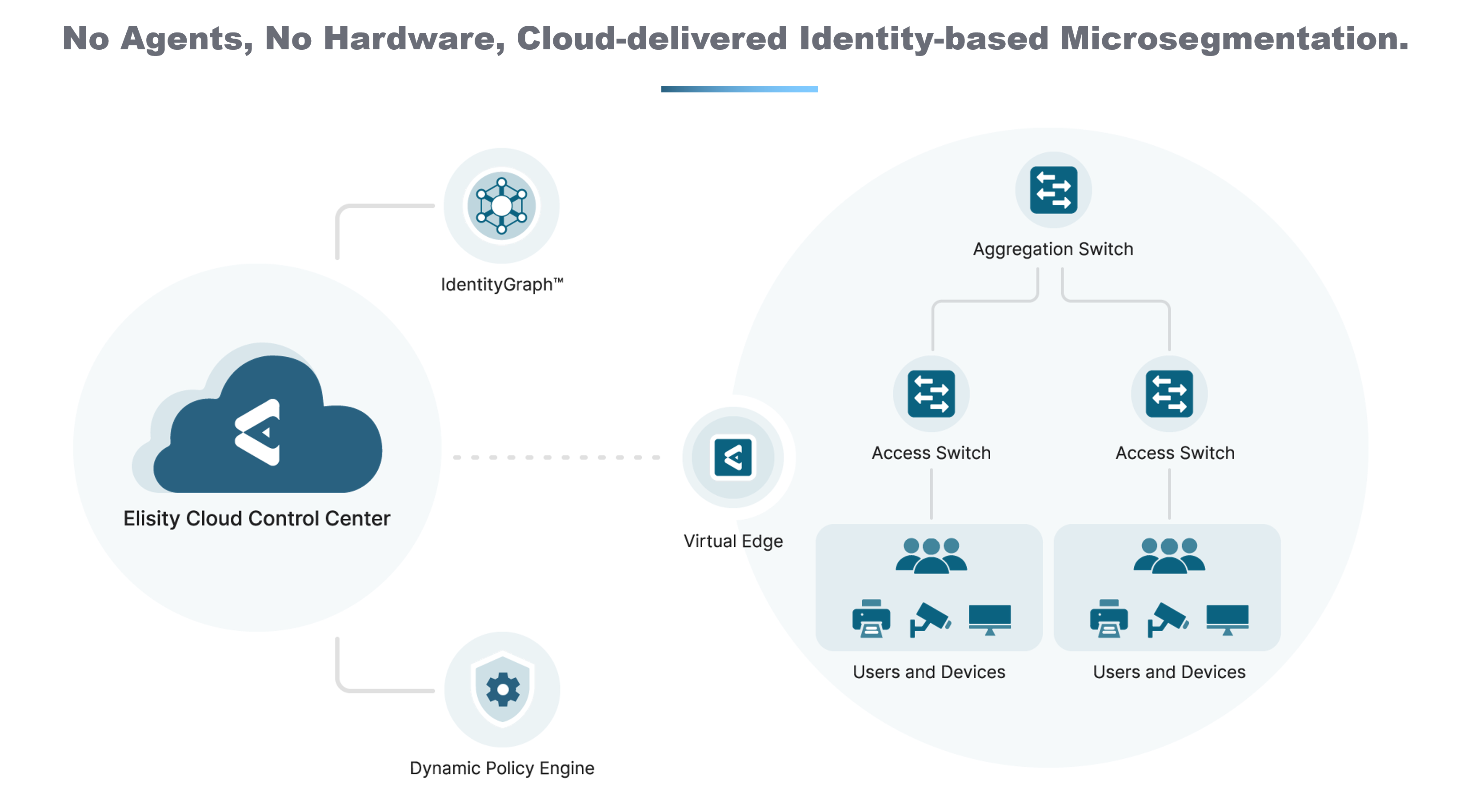
The Elisity IdentityGraph and the ability to microsegment the network further strengthens this approach. In combination, these features enable the creation of finely-tuned access controls which adapt in real-time, according to the context of the user's identity.
With respect to MFA, instead of managing these methods directly, Elisity's focus on identity and behaviour-based access control adds an extra layer of security. By ensuring that only the right identities have access to the right resources, it inherently bolsters MFA measures, even if they might be weak or misconfigured.
Hence, Elisity transforms how access control is viewed and implemented, stepping away from the conventional ACLs, and providing a more enhanced and suitably tailored level of network security.
Maintaining Credential Hygiene and Restricting Code Execution: Elisity's Approach
In the final findings from the Red and Blue team assessments, poor credential hygiene and unrestricted code execution emerge as prominent network misconfigurations. These issues offer a lucrative opportunity for the Red Team to seize control of a network or inject malicious code, respectively. Meanwhile, the Blue Team works diligently to enforce proper credential management and control over code execution.
Elisity addresses these issues by emphasizing secure access control. It enforces strict credential hygiene by ensuring that only verified identities can access critical assets. The IdentityGraph provides visibility into all active credentials, facilitating their efficient management. By granting access based on the context of an individual's identity and behavior, Elisity helps reduce the likelihood of credentials being misused.
When it comes to preventing unrestricted code execution, Elisity's microsegmentation and access controls play a crucial role. By blocking unauthorized access to critical assets, the chances of malicious code execution are considerably diminished. Hence, through tight control over access, Elisity indirectly helps to mitigate the risks associated with poor credential hygiene and unrestricted code execution.
Review: Mitigating the Top 10 Network Misconfigurations with Elisity
In conclusion, through advanced features like IdentityGraph, behavior-based access control, real-time visibility and agile microsegmentation, Elisity offers valuable solutions to tackle these misconfigurations identified by the NSA and CISA Hunt and Incident Response Teams assessments.
Embracing Elisity's approach means stepping away from traditional methods and moving towards a more granular, dynamic, and context-aware perspective of network security. While some of the solutions Elisity offers are direct, others are more indirect, but together they form a comprehensive approach to strengthening a network's defense against the constant threat of cyberattacks.
Organizations striving to improve their security posture now have the requisite knowledge to leverage Elisity's abilities in their favor, stepping up their Blue Team capabilities to match, if not surpass, the cunning of the Red Team.
Arm your organization with Elisity's next-gen cybersecurity capabilities to transform your network's security landscape! Get started with Elisity today.
Share this
- April 2024 (4)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)

No Comments Yet
Let us know what you think