Share this
I Wish We Had Elisity
by JP Cedeno on Feb 19, 2024 10:01:56 PM
One of the greatest things about Information Technology is its dynamic nature. As IT Professionals, we often find ourselves donning various roles throughout our careers. In my case, so far, it has been Architect, Instructor, Systems Engineer, Infrastructure Manager and more! The journey has certainly been diverse and filled with many insightful experiences.
As a Solutions Architect at Elisity, I have the privilege of sharing how our innovative technology helps customers solve various problems in their everyday lives. In this blog I would like to dive into one of the many chronicles of my career and discuss how Elisity would have saved a project that, at the time, ended in failure before it even began.
Segmentation / Network Refresh Project
Back in the mid 2000’s, I had the privilege of being the Infrastructure Manager for an organization that manufactured cosmetic products in upstate N.Y. I had never worked in such a diverse environment prior to this position. This facility operated 24/7/365 with operating lines that did everything from making plastic bottles that contained the product, to making every different cosmetic product you can think of. Each line with its own hardware, customized programming, and operational requirements. In addition to all of that, this was a mixed networking environment. Our team used to joke that it was the Frankenstein of networks.
One of the first projects I was tasked with was to upgrade the network to improve security to operate within the purdue model. Not only did we need to prevent cross traffic between levels, but also needed to segment based on the manufacturing zone, or line. In other words, an HMI at level 2 should never directly communicate with an HMI at level 3. However, if 2 HMIs were on the same manufacturing line, or within the same zone, they were permitted to communicate if necessary.
To even come close to achieving this, we would need to reroute all our traffic through multiple firewalls which would be strategically placed throughout the network to avoid bottlenecks and latency. Those firewalls would need thousands of IP based rules to restrict, or permit, access between devices. This also meant that each device would need a static address, or at least a static DHCP reservation.
In addition to these challenges, we would have to deal with vender lockouts. Most, if not all, of our production lines were built and delivered by venders who had exclusive administrative privileges to the gear operating on that line. The amount of time it would take to get all these different venders on site to add static addresses to each PLC, HMI, and sensor on the line wasn’t practical.
Lastly, we had a very robust wireless network that was built to accommodate all different types of devices and place them on different networks. For example, newer production lines that had wireless sensors had their own SSID which would land those devices into their own VLAN. Different SSID’s were used for guest devices, such as employee cell phones and tablets, while other SSID’s would handle company owned devices. But as you can imagine, passwords were shared, line operators taking issues upon themselves to resolve, and this soon became a mess…
It was becoming clear that this just wasn’t something that was possible to solve, especially in a short amount of time. Not just from a practical perspective, but from a financial perspective. Solving this would involve taking down the plant for an unknown amount of time, multiple times, resulting in loss of production and revenue.
So, let’s look at how Elisity would have helped us achieve our goal quickly and easily, without any downtime required.
Device Detection and Identification
Elisity is a software only, cloud hosted, segmentation platform that provides a robust solution for network security and management. The device identification capabilities leverage advanced algorithms and machine learning techniques, allowing the solution to accurately identify and classify devices connected to the network.
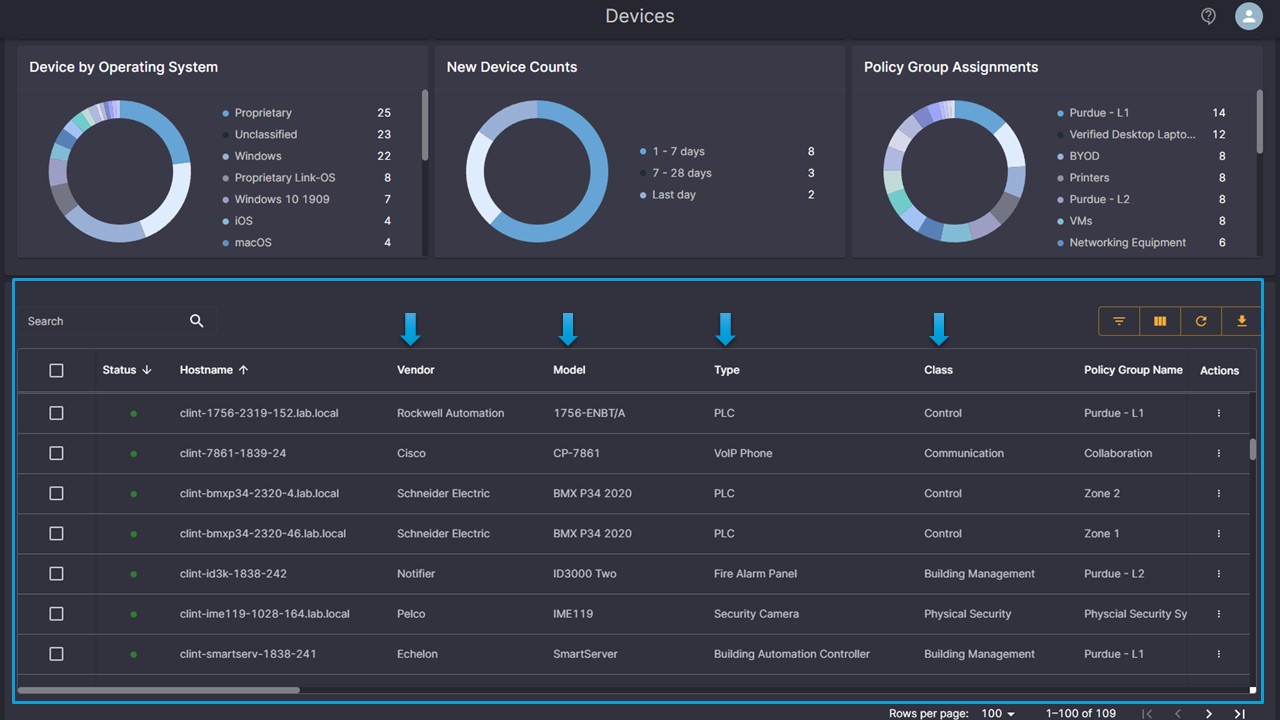
Elisity can distinguish between authorized and unauthorized devices using fingerprinting and identity data found in IdentityGraph, enabling proactive threat detection and mitigation. This granular visibility empowers organizations to enforce access policies, detect anomalies, and ensure compliance across their network infrastructure, thereby enhancing overall security posture and network performance.
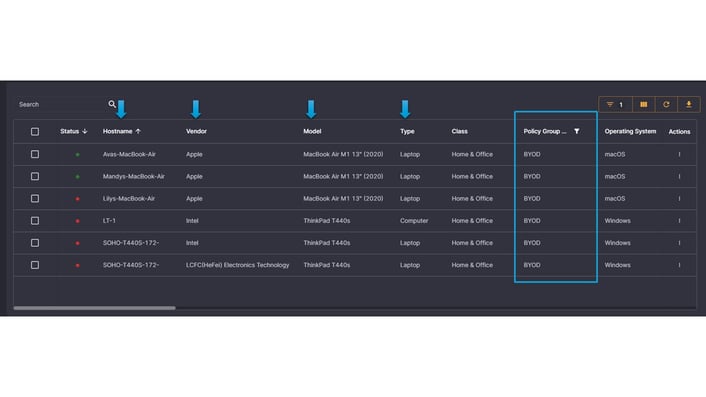 Elisity’s Identity Graph facilitates the correlation of data from various sources, such as ServiceNow, Claroty, Medigate, and others, empowering security teams to quickly identify and respond to threats, streamline incident investigations, and optimize network performance. This integrated approach not only enhances security posture but also fosters operational efficiency and agility across the entire organization. By incorporating IdentityGraph technology, Elisity creates a comprehensive map of network entities and their relationships, enhancing the contextual understanding of security incidents and operational events.
Elisity’s Identity Graph facilitates the correlation of data from various sources, such as ServiceNow, Claroty, Medigate, and others, empowering security teams to quickly identify and respond to threats, streamline incident investigations, and optimize network performance. This integrated approach not only enhances security posture but also fosters operational efficiency and agility across the entire organization. By incorporating IdentityGraph technology, Elisity creates a comprehensive map of network entities and their relationships, enhancing the contextual understanding of security incidents and operational events.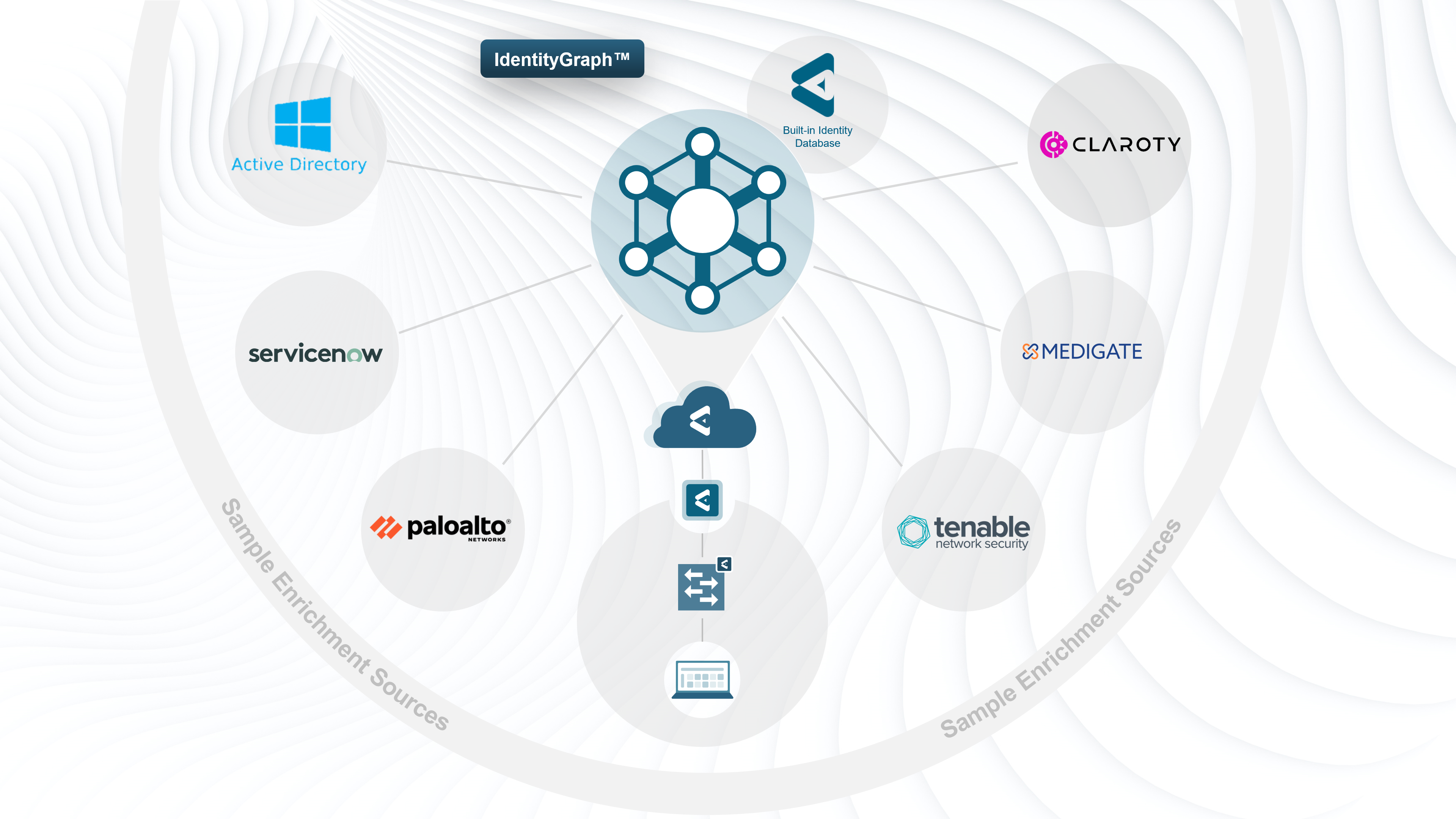
Configuring these integrations within Elisity is very straightforward. Navigating to the connectors page within the UI, administrators simply need to select “Add Connector”, select the desired integration, and provide the API credentials and URL that are required. That’s it!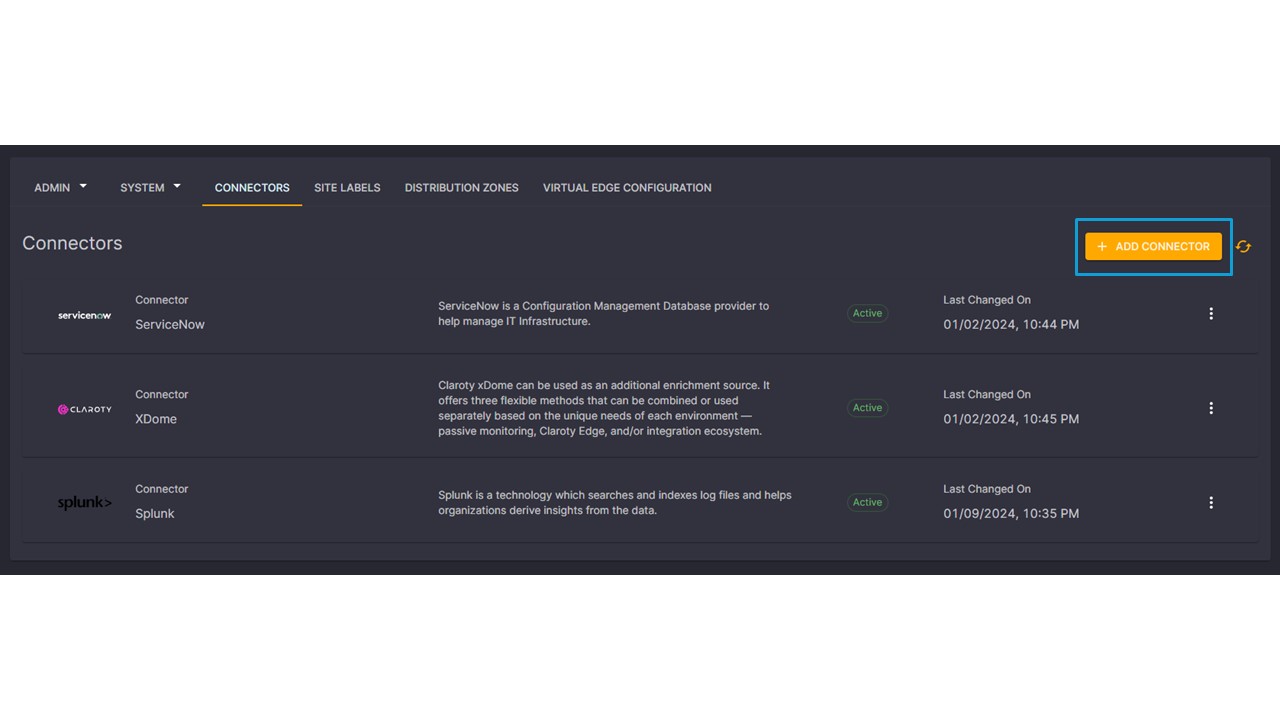
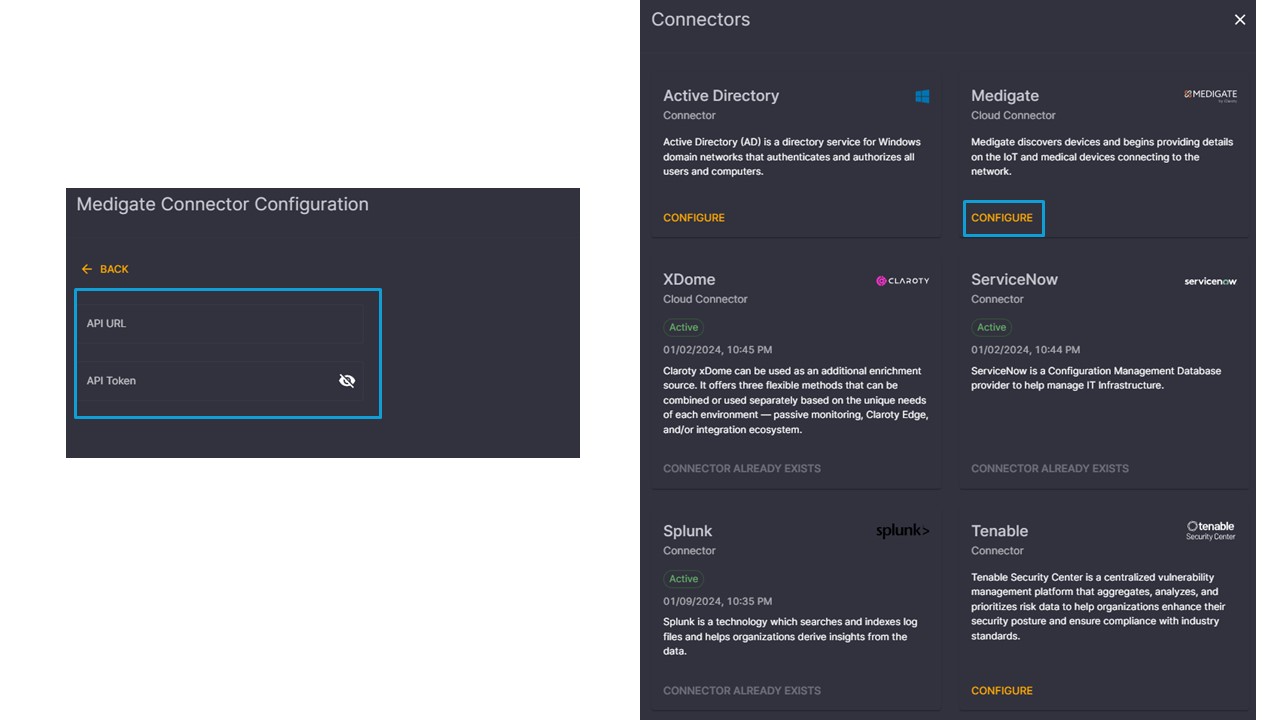
From here, the platform automatically combines data it has natively collected, with the various other systems of records, into its IdentityGraph with the goal of utilizing this data for policy outcomes.
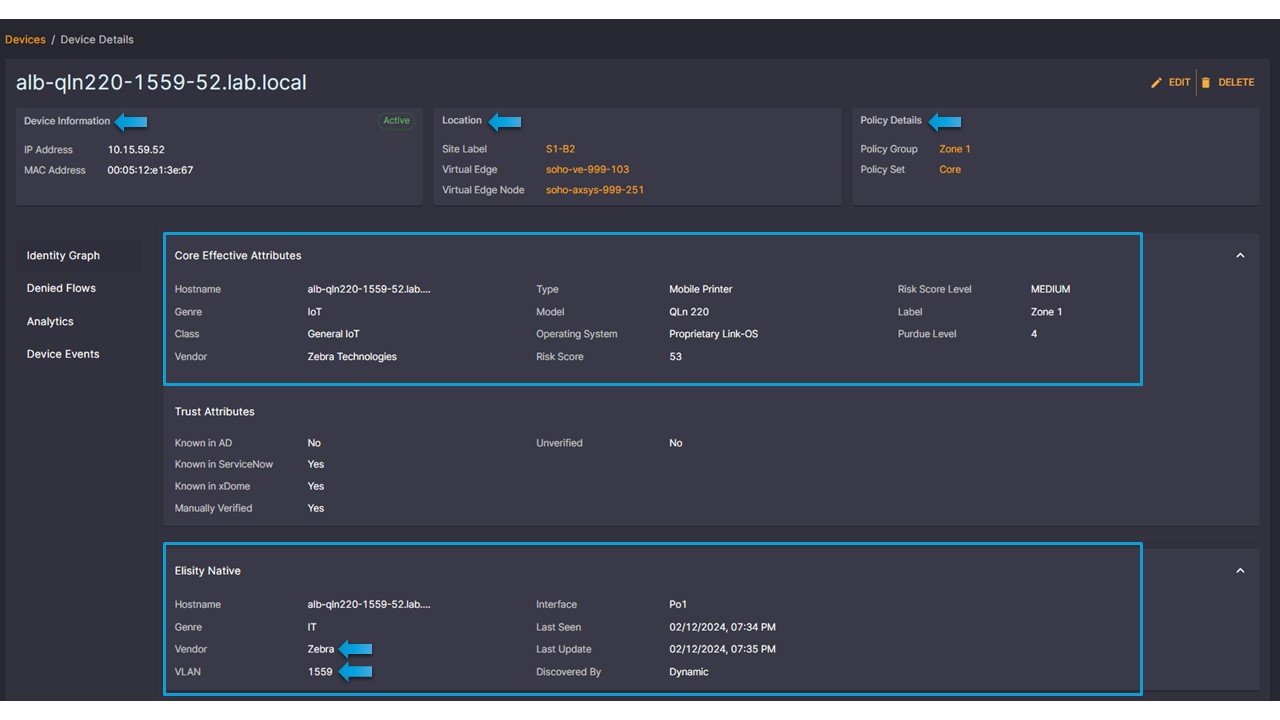
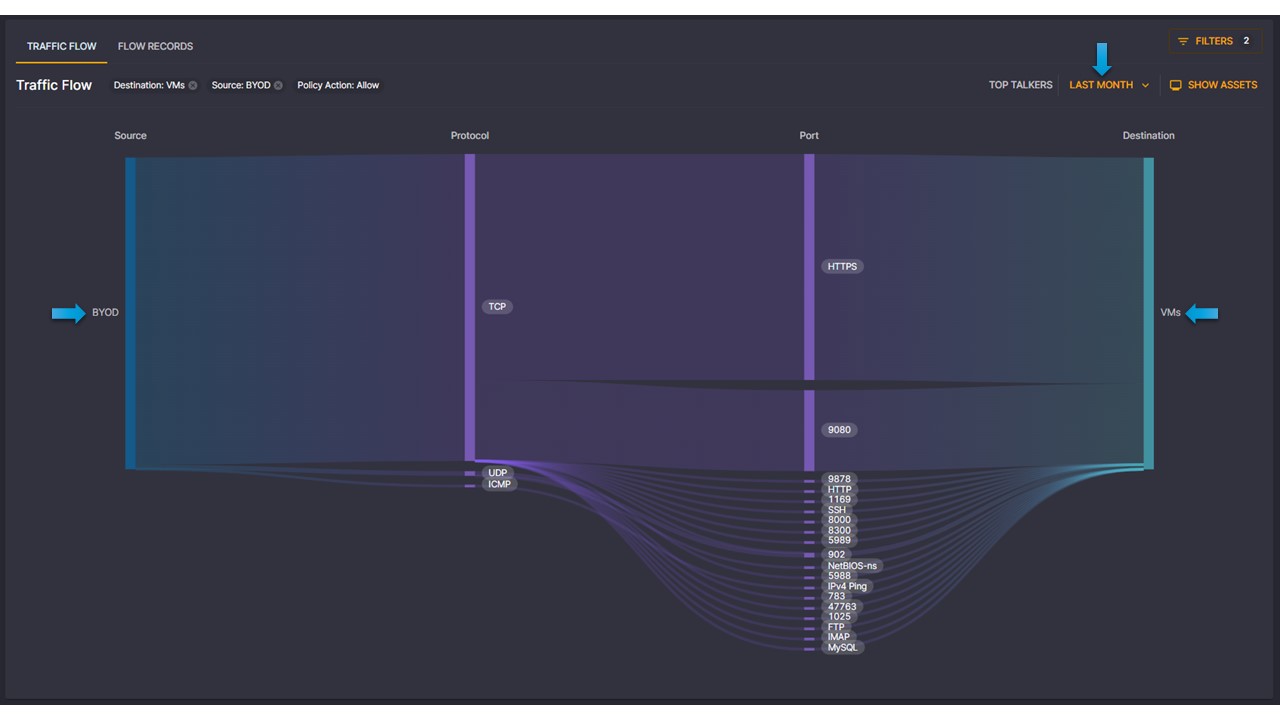
Through advanced monitoring techniques, Elisity can accurately capture and analyze traffic patterns, identifying sources, destinations, and types of data traversing the network in real-time. This granular insight would not only enable the organization to detect potential security threats, monitor application performance, and optimize network traffic, but more importantly make an educated and informed decision on segmentation policies. This analytics data between Policy Groups and the assets within are critical to understanding the complex relationships between assets on your network, and how to secure them without inhibiting crucial traffic flows required for your operations.
Turning data into policy
Having all this data is amazing, but the whole point is to have meaningful policy outcomes that make a difference and solve the problem statement. Elisity leverages existing network infrastructure to enforce least privilege access policies through its innovative approach to network security. By integrating with the existing network, Elisity allows organizations to implement granular access controls, ensuring that users and devices only have access to the resources and applications necessary for their roles and responsibilities.
The first step in this process is Elisity’s ability to create policy groups, which offer a streamlined and dynamic method for managing access controls within network environments. Policy groups provide organizations with the ability to automatically classify users, devices, and applications into logical groups. With Elisity's policy groups, organizations can quickly adapt to changing business needs, implementing and adjusting access controls with agility and precision. Even the ability to identify rogue network devices, or devices within a Purdue level or zone is easily achievable with the click of a button.
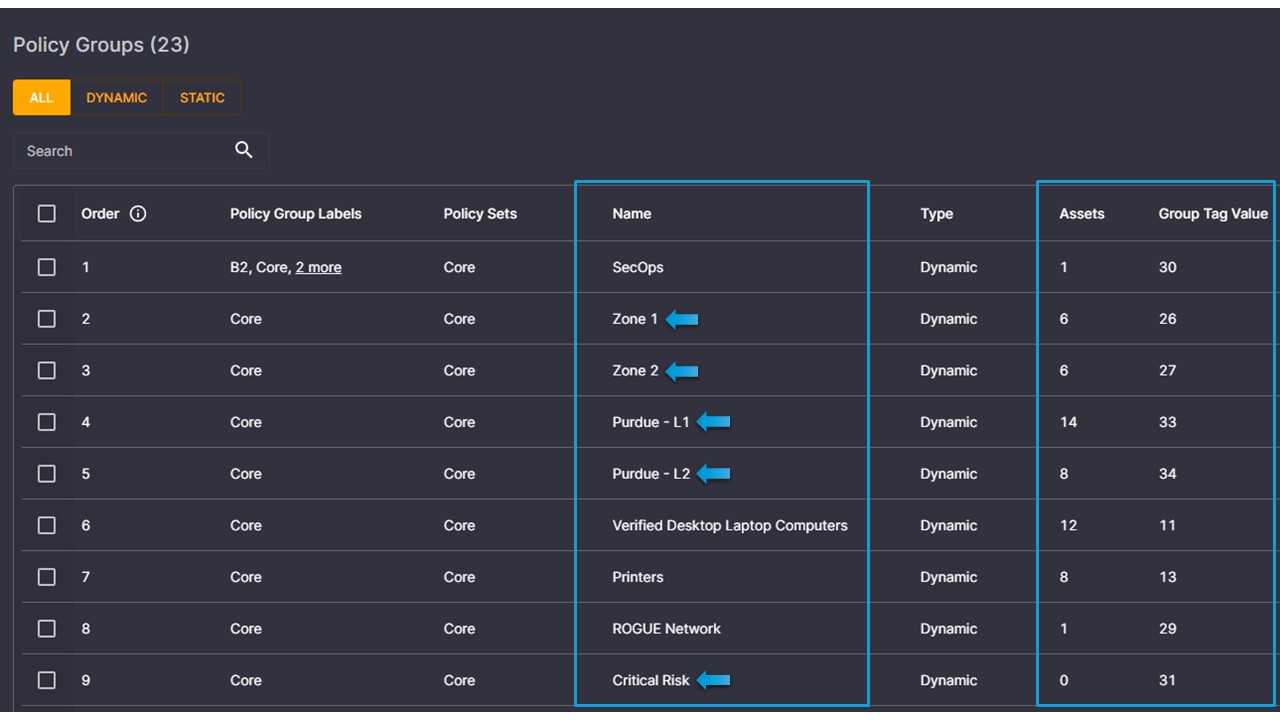
Just like configuring integrations is seamless, so are the creation of policy groups! From the Policy Group page, we can select “Create Policy Group” and select “dynamic”.
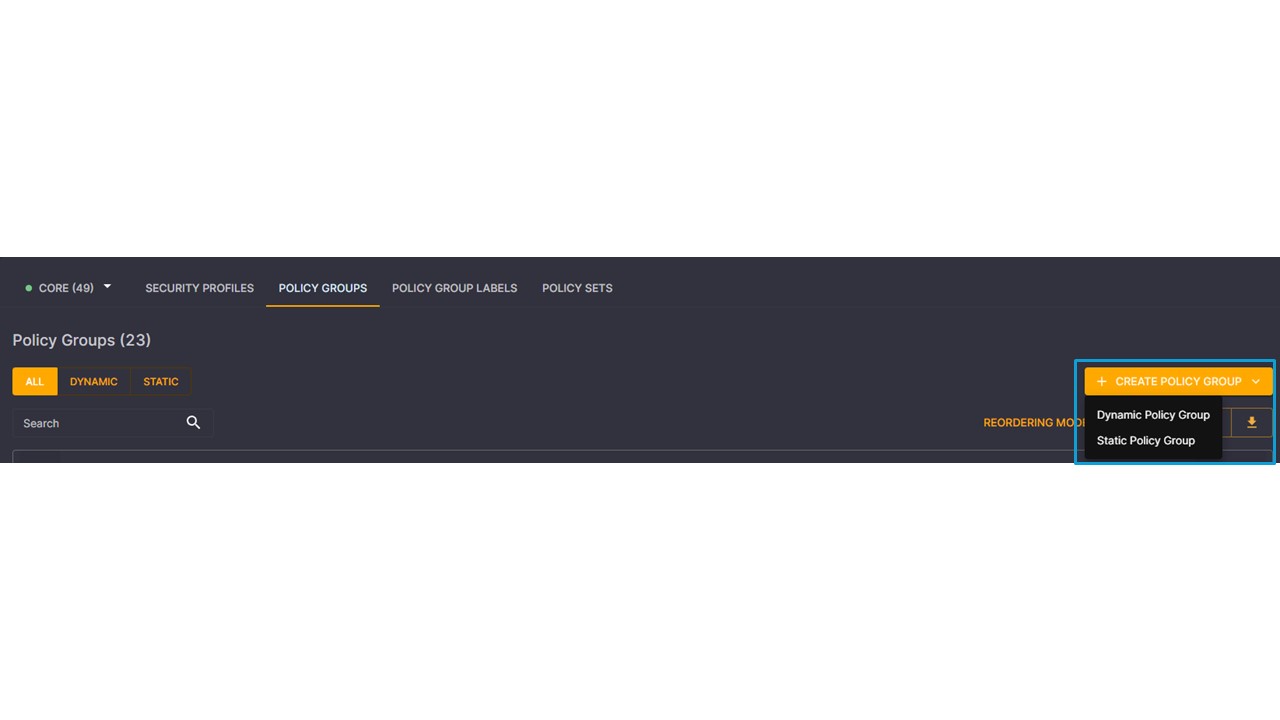
Under the criteria, all we have to do is select the data to use in order to dynamically populate this group with devices on our network. Attributes can come from any of these sources, or all of them! We have complete control in how we want our group to be defined.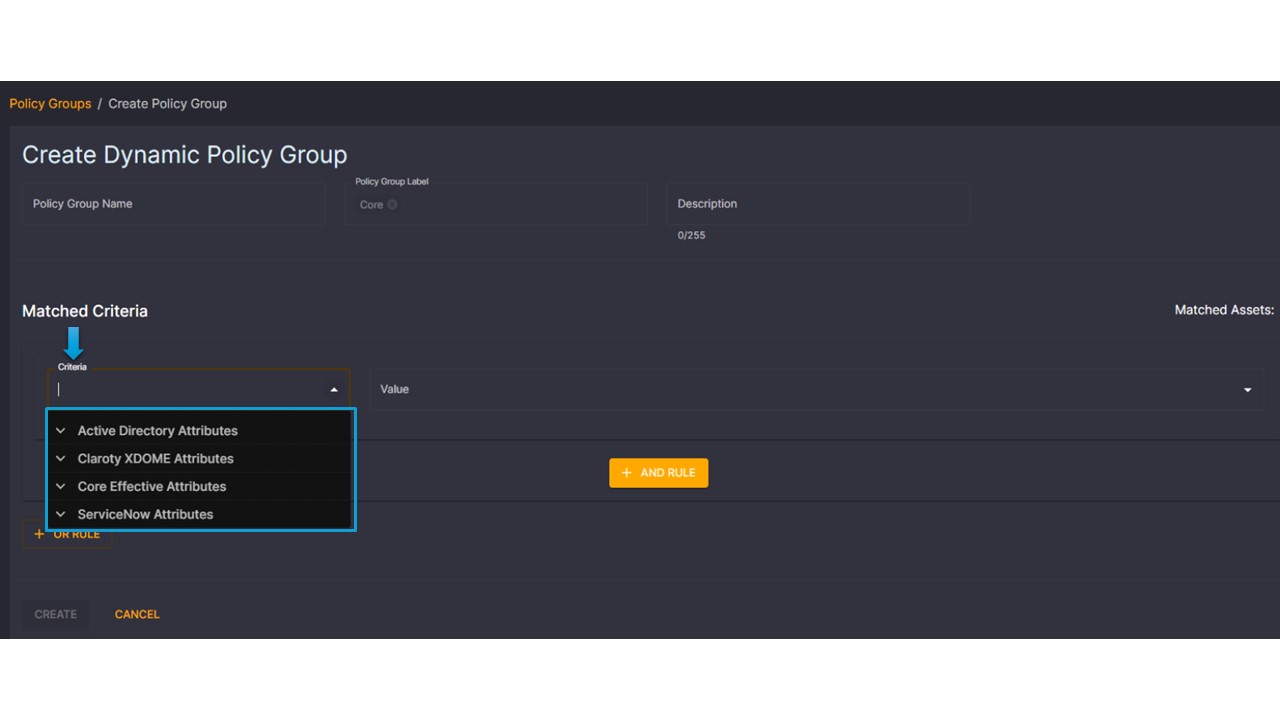
I want to stop here and collect our thoughts. I had been tasked with segmenting our network and with the technology of the time, it was impossible. But now, in 2024, at my fingertips is a system that can dynamically identify, in real time, devices on my network that are BYOD vs. Corporate owned and automatically place them into different policy groups. By expanding the Claroty xDome category, I can even become more granular by creating policies based on risk scores!
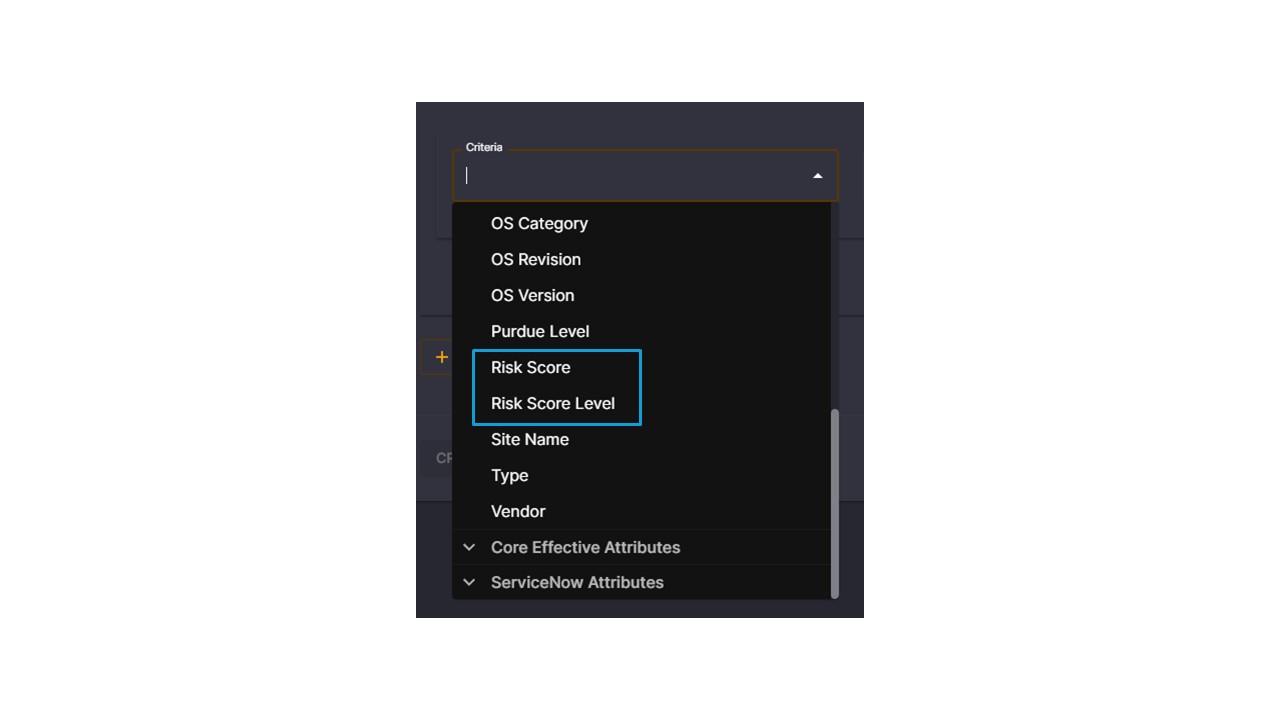
Now I have a system that can easily define which devices belong to which production lines, and which devices belong to certain Purdue levels, and prevent access between zones and levels. Once these policy groups are defined, the only thing left to do is create a simple policy in our network that prevents these different zones or levels from communicating, which is easily done within the policy matrix.
Elisity's policy matrix provides a comprehensive framework for defining and managing access policies across diverse network environments. This empowers organizations to create tailored access policies based on factors such as user roles, group memberships, contextual attributes, device types, and other key factors, fostering a flexible yet robust security posture.

Selecting the intersection where policy groups meet allows us to create any type of policy required for the devices within that group. Policies can be typical zero-trust network access policies, or they can simply deny particular ports and protocols while allowing all other traffic.
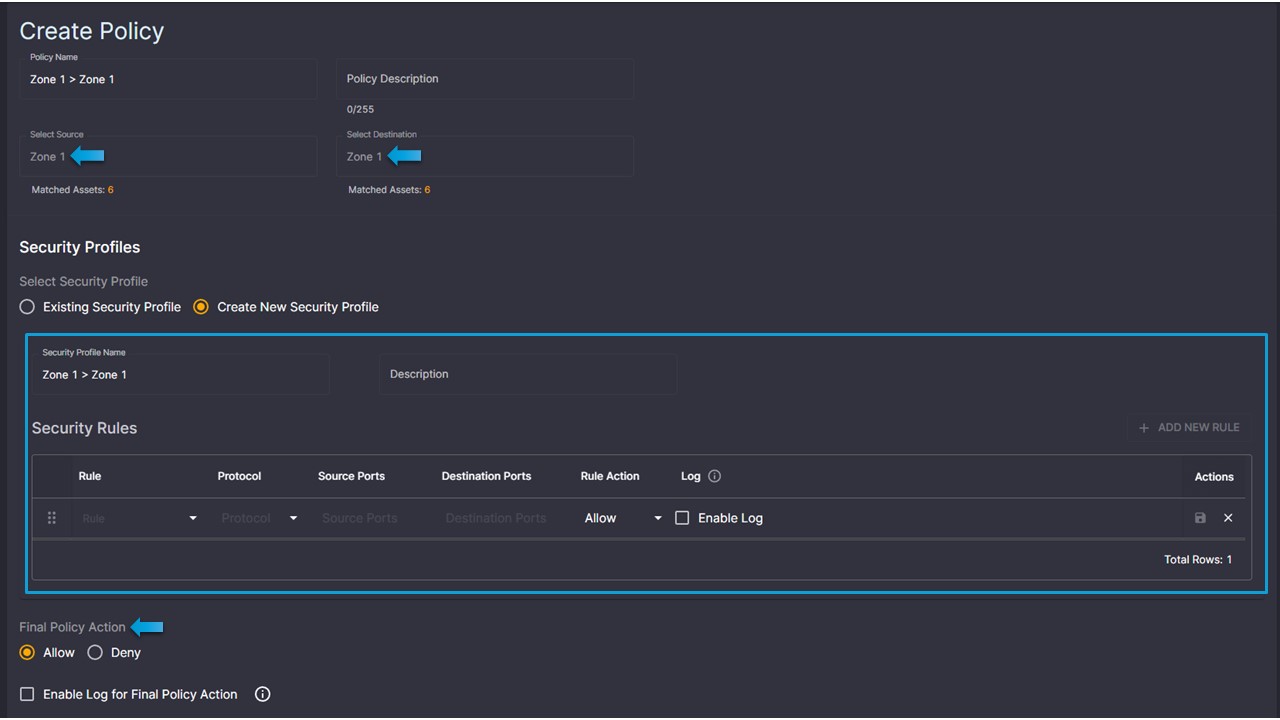
By providing comprehensive visibility into all network assets and enabling segmentation without the need for extensive network re-architecture, Elisity would have empowered the facility to enhance its security posture while maintaining operational efficiency.
As industries continue to navigate the complexities of modern cybersecurity challenges, solutions like Elisity offer a beacon of hope, enabling organizations to proactively defend against cyber threats and safeguard their digital ecosystems with confidence. If you are struggling with network visibility or segmentation, schedule a demo today. I promise you will not be disappointed.
Additional Resources:
Share this
- April 2024 (2)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)
No Comments Yet
Let us know what you think