Share this
Mitigating Threats from BianLian Ransomware: A Response CISA Advisory
by Dana Yanch on Jun 1, 2023 8:09:37 AM
In light of the recent joint Cybersecurity Advisory (CSA) issued by the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and Australian Cyber Security Centre (ACSC), it has become critical for all cybersecurity professionals to take note of the rising threats from the BianLian ransomware and data extortion group. The advisory, as part of the ongoing #StopRansomware effort, aims to arm network defenders with detailed information about various ransomware variants and threat actors, including recently and historically observed tactics, techniques, procedures (TTPs), and indicators of compromise (IOCs).
Understanding the Threat
The BianLian group, a ransomware developer, deployer, and data extortion cybercriminal group, has been targeting organizations in multiple U.S. critical infrastructure sectors since June 2022. They have also extended their operations to Australian critical infrastructure sectors, professional services, and property development. The group's modus operandi involves gaining access to victim systems through valid Remote Desktop Protocol (RDP) credentials, using open-source tools and command-line scripting for discovery and credential harvesting, and exfiltrating victim data via File Transfer Protocol (FTP), Rclone, or Mega. The threat does not stop there: the BianLian group then extorts money by threatening to release data if payment is not made. What's notable is that the group has shifted its focus from a double-extortion model, where they encrypted victims' systems after exfiltrating the data, to primarily exfiltration-based extortion since January 2023.
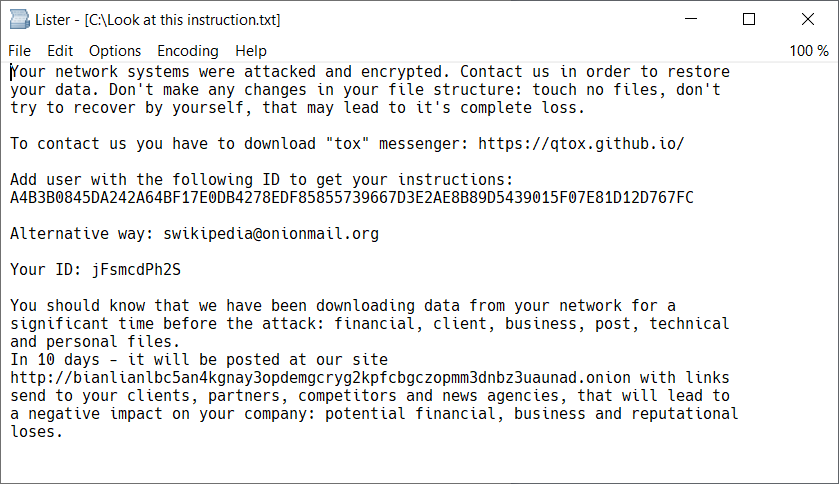
Mitigating the Threat: A Deeper Dive
The joint Cybersecurity Advisory has recommended several actions to mitigate cyber threats from the BianLian ransomware and data extortion group. Let's take a deeper dive into these measures and understand why they are effective:
- Strictly limiting the use of RDP and other remote desktop services. By tightening control over these services, we significantly reduce potential entry points for the group. This is because the BianLian group often gains access to systems through valid RDP credentials.
- Disabling command-line and scripting activities and permissions. This measure prevents the group from using these tools for discovery and credential harvesting. It is essential to note that this group has been known to exploit these tools, making this a highly effective countermeasure.
- Restricting the usage of PowerShell and updating Windows PowerShell or PowerShell Core to the latest version. The BianLian group might deploy PowerShell-based attacks. By restricting its usage and ensuring your systems are updated, you make them less vulnerable to these attacks.
It's important to note that these are not theoretical recommendations but have been effective in real-world situations. By implementing these measures, numerous organizations have successfully mitigated threats from BianLian and similar ransomware groups.
In addition to these specific measures, it is also crucial to maintain a robust security posture, including regular security audits, continuous monitoring of network activities, and prompt patching of software vulnerabilities.
What Next?
In an era marked by relentless cyber threats, it's vital to stay ahead of cybercriminal groups like BianLian. Is your organization prepared to respond swiftly and decisively?

At Elisity, we understand the urgency of these challenges. We offer software-only, rapid deployment solutions that transform how you implement least privilege policies. This means you can act fast, safeguard your business operations, and get back to doing what you do best.
If you're seeking to enhance your security strategy or need personalized advice on securing your infrastructure against threats like BianLian, we're here to assist.
The battleground of cybersecurity is constantly shifting, with the tactics of threat actors like the BianLian ransomware group evolving at every turn. Being informed and vigilant is key to defending your systems and data against such threats. With Elisity at your side, let's turn the tables on cyber threats together. Stay safe, stay secure, stay proactive.
Share this
- April 2024 (1)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)

No Comments Yet
Let us know what you think