Share this
Understanding Forrester’s Zero Trust Edge Architecture
by Sundher Narayan on Mar 19, 2021 6:51:35 PM
Corporate data is everywhere. Employees, customers, and partners are constantly accessing, emailing, copying, syncing and sharing data wherever they happen to be. This makes knowing where sensitive data is stored and who has access to it rather difficult to manage.
With networks often-times connecting to multiple cloud services, users access resources over different WANs and devices simultaneously. Some users will fall under your policy net, but others won’t. This raises the question:
How do businesses successfully enforce policy and compliance standards under these anywhere/anytime conditions without affecting network performance?
A recently released report from Forrester Research Inc., Introducing The Zero Trust Edge Model For Security And Network Services, highlights the need for a Zero Trust Edge (ZTE) to help unify the networking, and the security specific infrastructure needed to maintain the business networking fabric.
According to Forrester1, ZTE has proven to be the most effective at securing and enabling remote workers. But first, let’s look at the alternatives to ZTE; Proxies and VPNs.
Proxies and The Distributed Enterprise
Today’s proxy solutions work in one of two ways: 1) proxy serves as a traffic forwarder to a centralized firewall, or 2) proxy is performed as full in-line inspection at the entry point – either network entry on the VPN or in the cloud edges. It’s often incorrectly assumed that cloud-based inspection requires proxy, but this isn’t quite the case. To assume edge inspection of every data flow on every connection is not only a massive strain on the network, it’s also not scalable. Simply throwing compute/network resources to achieve line rate throughput/performance and desirable latency metrics is possible, but it significantly affects cost of ownership.
Additionally, since proxies force all traffic into a shared security filter (with policy pre-written), the setup commonly results in users experiencing app slow-downs due to the network traffic jams, and distance-based latency introduced by an overloaded network. IoT data has compounded this strain on the network, as this influx of data to the proxies requires extensive resources (bandwidth, cost, operations, management), as every transferred packet to be decrypted, analyzed, and re-encrypted.
Solving these throughput and latency issues requires expensive network resources and infrastructure, not to mention the complexity and cost of management. Fortunately, ZTE presents a better approach by not assuming in-line proxy all the time, but rather, proxy is performed dynamically and intelligently when it’s needed.
Virtual Private Networks (VPN)
For a period of time, VPNs were the easiest way for organizations to provide secure connections to resources. Now, in the hyper-connected age, and with the amount of remote work still taking place, VPNs are cumbersome and difficult to manage. Networking and security teams are challenged with meeting the requirements of home workers because traditional approaches were based on on-site dedicated software or hardware, disjointed security and network silos, and unreliable on-prem controls and policy repositories.
VPNs have proven unable to scale with spikes in demand, especially with remote workforces seeming to be the new normal, even post-pandemic. Scaling this model requires physical network appliances with complex connectivity changes inside and outside the enterprise network, as well as traffic orchestration through the added VPN appliances and replication across site locations.
VPNs also present issues with connectivity, as enterprises require on-demand, low latency and highly available access. Security, in terms of both access protection and attack prevention, should be more adaptive than VPNs allow.
For these reasons, the industry has shifted its approach away from VPNs and traditional proxy strategies and are quickly moving towards the Zero Trust Edge.
Zero Trust Edge
When COVID-19 caused the remote workforce to exponentially grow, the Zero Trust Edge was born from a forward-thinking group of security professionals who believed traditional approaches weren’t the best way forward. Now recognized by Forrester1, ZTE is defined as:
“A Zero Trust edge solution securely connects and transports traffic, using Zero Trust access principles, in and out of remote sites leveraging mostly cloud-based security and networking services.”
Secure Access Service Edge (SASE) has emerged as a solution to the challenges a traditional proxy solution faces by means of Zero Trust access to SaaS applications, privately hosted applications, and the Internet. A SASE solution pairs networking with security services, all delivered from the cloud, including a variety of technologies like Cloud Access Security Broker (CASB), Zero Trust Network Access (ZTNA), Firewall as a Service (FWaaS), and advanced threat protection, among others.
Zero Trust Edge with Selective Inline Inspection
The desire for need based inline inspection arose from the modern enterprise’s dispersion of applications and data, paired with an exponential increase in remote connectivity needs requiring the best levels of throughput, performance and latency. With ZTE implemented, proxy is performed on the ZTE nodes as needed, based on an ecosystem that starts from building intelligence at the source of the data and integrates continuous identity verification as needed, as shown below.
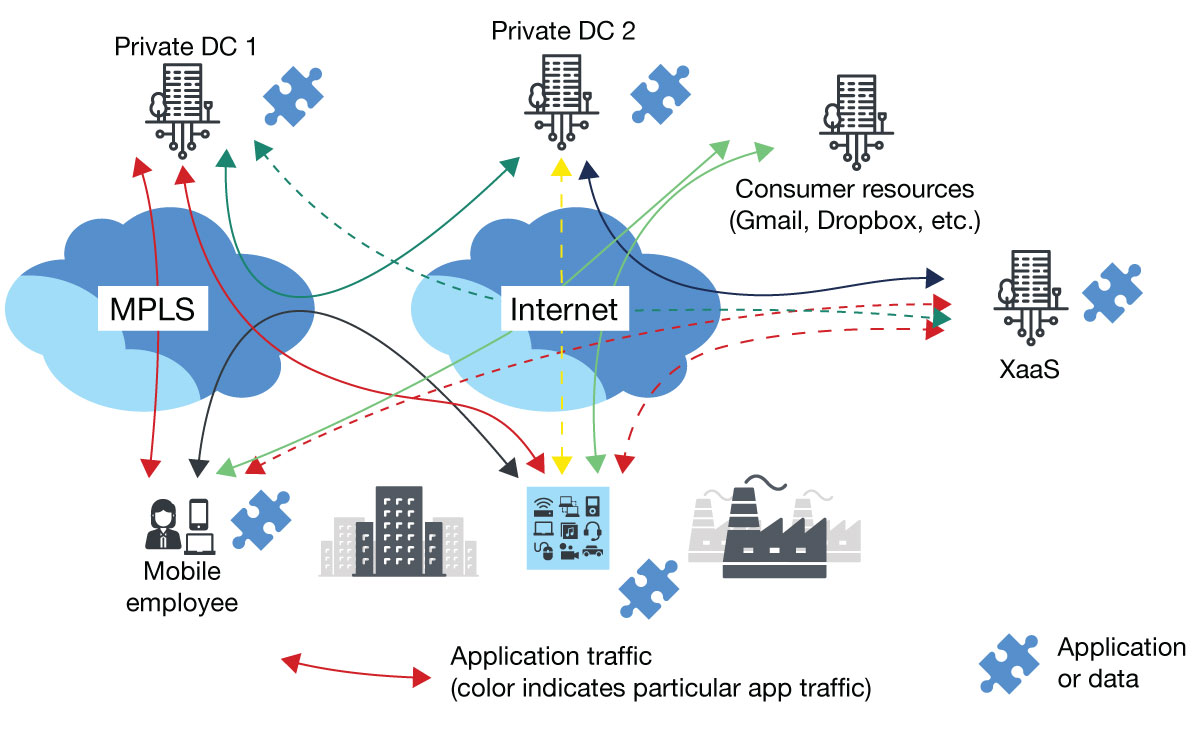
An intelligent approach does not eliminate the need for in-line proxy or data inspection, but rather, determines when to perform it. With intelligent proxy, security policies require traffic to meet trust levels. When traffic does not meet the necessary minimums, it must be inspected. The big difference is that in-line proxy is intelligently performed only on infected or unauthorized traffic. This saves massive network resources and bandwidth, as every single packet of transferred data does not need to be proxied.
Zero Trust Edge in Practice
The paradigm of securing resources has changed from securing the network holistically, to securing devices, apps, and data, individually. A SASE solution ensures that the right people have access to the right things. In other words, holes can’t be punched into the firewall to open-up the perimeter so trusted users can gain entry without risking intrusions from malicious actors as well.
Instead, it must be assumed that users and devices are untrusted, by default. Entitlement-based “right size” access to resources for only specific, verified users ensures that even in the rare event that a device is compromised, the attacker could never laterally travers to other places in the network.
According to Forrester1, a ZTE Solution enables the following services and capabilities1:
Network
| Bandwidth guarantee | Sets a minimal amount of bandwidth for particular traffic |
| Content caching | Provides localized copies of data |
| Link balancing and utilization | Leverages multiple links simultaneously to increase traffic bandwidth and overall WAN utilization |
| Quality of Service | Prioritizes network traffic |
| Resiliency | Delivers and maintains an acceptable level of service in the face of faults and challenges to normal operation |
| Routing/best path | Selects the right path for layer 3 transport even from the remote worker to a cloud-hosted application |
| Software-defined WAN (SD-WAN) | Chooses the best paths, links, or connections based on higher level metrics, such as jitter, dropped packets, and affinity to an application profile |
| WAN connection | Establishes the physical connection to/from a facility |
| WAN optimization | Provides deduplication, packet coalescing, and other WAN optimization features |
Security
| Basic firewall | Offers simple network firewall capabilities (layer 3 and 4 rules) that can be split off and moved locally to reduce the amount of traffic exiting the remote facility |
| Cloud access security broker (CASB) | Controls and reports on cloud application access |
| Firewall as a service (FWaaS) | Provides cloud-based advanced firewall features and functions |
| Intrusion detection | Analyzes network traffic based on signatures to detect and deflect specific malicious content |
| Link encryption | Encrypts and decrypts all network traffic at each network routing point |
| Identity and access management (IAM) | Ensures that the proper people in an enterprise have the appropriate access to technology resources |
| Secure Web Gateway (SWG) |
Prevents unsecured traffic from entering an internal network of an organization. URL filters must be constantly updated, and the trend was already to have these configured, hosted, and maintained in the cloud
|
| Advanced malware analysis | Runs programs in a secluded environment (sandboxing) to screen and contain zero-day malware types |
| Zero Trust Network Access (ZTNA) | Enables the remote worker to connect to enterprise applications based on their identity regardless of where the workers or the applications reside. It is the signature security service that must exist in the ZTE. |
An intelligent Zero Trust Edge is how organizations today are significantly shoring up their network defense strategies without data center security experts needed to rip and replace infrastructure or implement complex new software. IoT and remote work have presented major security concerns; ZTE protects edge computing frameworks and guards against known and unknown attackers. It’s also an architecture that scales with the network to protect from unauthorized access.
Many enterprises are looking at the ZTE model to strategically solve 2020’s biggest security challenge: the remote workforce. More VPN licenses or network bandwidth for proxy services may have been a stopgap measure to keep people connected and working in the interim. A year later, with remote work becoming the norm, ZTE is the obvious long term solution.
While ZTE came to fruition as a way to better secure the remote workforce, in the end, remote offices, branches, manufacturing plants, factories, and data centers will all be connected to the ZTE network to intelligently authorize, monitor, and protect network traffic.
Download the full January 28, 2021 Forrester Report, Introducing The Zero Trust Edge Model For Security And Network Services.
Share this
- April 2024 (2)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)
No Comments Yet
Let us know what you think