Covid-19 caused organizations to sprint towards a remote workforce at an incredible pace. Now, that sprint has turned into a marathon, as more businesses are leaning towards keeping the majority of their workforce remote for the foreseeable future. The new normal is no longer temporary.
As organizations have moved towards work-from-home (WFH) as the new normal, they’ve discovered the inadequacies of legacy remote access solutions – in particular, VPN – that left them exposed to cyber-attacks. VPN technology has proven inherently insecure, and comes with numerous limitations:
- Risk of lateral movement: Remote users are typically placed directly onto the internal network, which means that compromised end user machines can potentially access the entire network
- Limited visibility and reporting on VPN traffic flows, especially for SaaS and Cloud traffic
- Minimal segmentation with VPN filters, with little precision and zero automation of network policies
- VPNs lack the security layers required to secure an enterprise, making them easy targets for hackers
 With the rising need for remote workforce security, one strategy has come to the forefront – Zero Trust – a system that moves security to every level of a network, instead of just at the login or “perimeter.” Zero Trust couldn’t have come at a more opportune time.
With the rising need for remote workforce security, one strategy has come to the forefront – Zero Trust – a system that moves security to every level of a network, instead of just at the login or “perimeter.” Zero Trust couldn’t have come at a more opportune time.
By controlling access to applications, systems, and resources, alongside the assumption of a continual breach, Zero Trust enables more robust security for all. Zero Trust is an IT Security model that requires strict identity verification for every person and device attempting to access a private network (on prem or Private Cloud), regardless of whether they are sitting within or outside the network perimeter.
Retire your Legacy VPN with Elisity Access Service
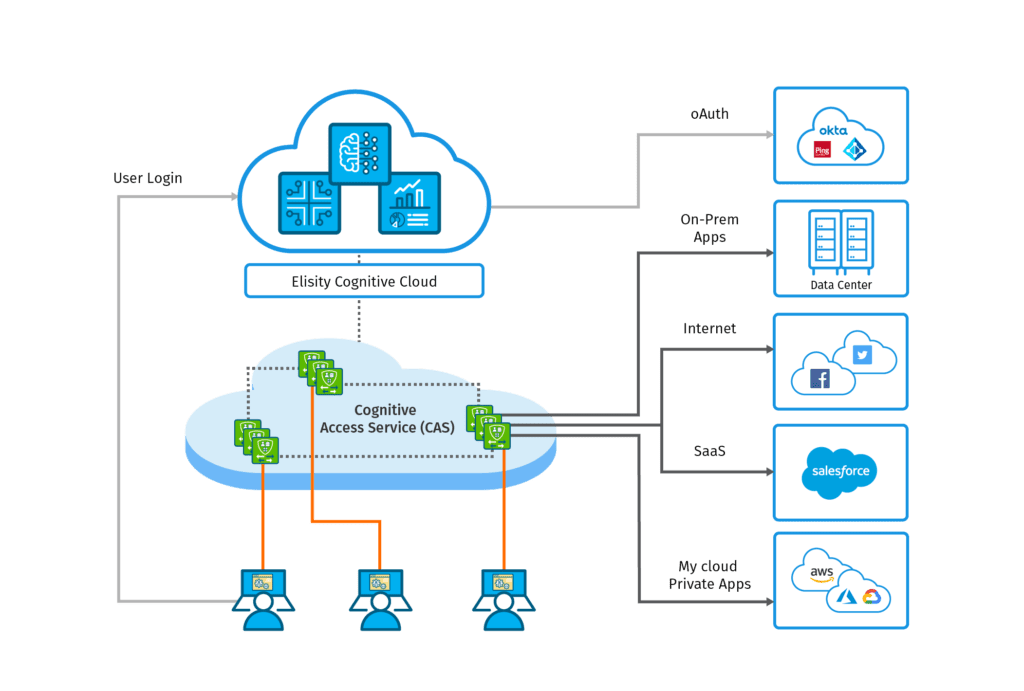
Elisity Access Service was designed from the ground up to address the challenges presented by remote access. Using both a Software-Defined Perimeter, and Zero Trust Network Access, Elisity Access Service creates rapid, secure, “right-sized” connections for remote users to both on-prem and cloud-based applications and resources. Elisity Access Service enables organizations to achieve both adaptive access protection and attack prevention.
With highly granular, application-level access controls, Elisity Access Service ensures that no user can connect to any application or resource unless they are explicitly permitted – but can connect immediately, with outstanding quality of service, when they are permitted. Elisity Access Service works with both web apps and enterprise applications, and is a holistic solution, empowering organizations to retire their VPN point solutions.
Elisity Access Service is an Elisity-managed, cloud-delivered remote access service with a global backbone that allows remote users to connect to the nearest region from anywhere in the world, for better performance and quality of service. In addition, Elisity Access Service:
- Implements and enforces identity-based policy pushed from the Elisity Cloud Control Center
- Provides policies without decrypt-encrypt cycle
- Can provide network functions such as QoS, path selection, and routing
- Provides security posture and protection based on behavior and context
- Integrates with security capabilities such as DLP, FWaaS, threat prevention, and more
- Securely connects users to applications in Cloud, data center, Public Cloud, or SaaS
- Integrates with SIEMs to provide comprehensive logging and user behavior metrics
Elisity Remote Access
The simple fact is that while identity can be hacked and forged, behavior cannot. A security posture based on behavior and context is vital to the next generation of enterprise security.
Until now, Zero Trust strategies required in-depth implementation by security engineers. But thanks to Elisity Access Service, any organization can easily and efficiently take advantage of the benefits of a Zero Trust security system on their network, without the need for advanced programming and engineering skills.
To learn more, please visit our Remote Access with Elisity Access Service Use Case.
Or, request a demo of the Elisity Cognitive Trust platform, and see for yourself how Elisity Access Service can transform your security strategy.
No Comments Yet
Let us know what you think