Share this
Tackling Enterprise Network Challenges with Elisity: Transforming Asset Inventory and Policy Management Through Automation
by Taylor Colwell on Sep 5, 2023 12:57:18 AM
Navigating the Complexity of Modern Networks
Modern enterprise networks present a formidable challenge. Organizations often find themselves juggling a combination of old and new technologies, trying to balance business operations and high availability with least privilege access, compliance standards, and the protection of business-critical assets. Consider a hospital or a manufacturing plant that contains highly sensitive, business-critical systems as well as miscellaneous IT and IoT assets. Then factor in a diverse workforce requiring varied network access. The task of securing large scale environments such as these is nothing short of herculean.
In the past, securing these types of environments was a manual process. IT professionals found themselves buried in lines of configuration code, assigning and reassessing access rights for users, devices, and applications, often in an ad-hoc manner. This time-consuming, human-error prone process has always left a backdoor open to various security vulnerabilities.
Keeping Up with Security Demands
Automating processes such as asset identification, classification, and policy enforcement is becoming a requirement. Automating these processes with confidence, and at a speed that can keep up with the requirements of an ever-evolving network is a roadblock for many on the microsegmentation path.
Just the simple process of creating a single source of truth for what assets are found on your network, which is absolutely required for confidently enforcing least-privilege access, is a task that most organizations simply cannot complete. Now imagine trying to keep that source of truth up to date day to day.
The relationship between technology and security becomes more complex with higher risk as networks grow and evolve. For example, industrial machinery, previously manually operated, is now controlled remotely with connections to a network of sensors and interfaces. Many times, connections to external networks are a requirement, further opening up the potential for vulnerabilities. Thus, what was once a straightforward operation is now a complex orchestration of people, machines, and network policies. The network becomes the linchpin of these complex interactions, making robust identity and policy management an existential requirement.
Many organizations that have made an attempt to modernize their network security have been left searching for a solution that elegantly combines identity management, visibility, and microsegmentation functions, but the truth is that most solutions with these offerings turn out to be quite unwieldy. The outcome is often a hodgepodge of various solutions that don't integrate well, leaving security teams managing multiple solutions all while never fully reaching their goal of microsegmentation.
Enter Elisity: A New Paradigm in Policy Management
Elisity significantly streamlines this complexity. At its core, Elisity automatically aggregates identity data and telemetry to form a foundational asset inventory for your microsegmentation efforts. "Assets" in this case refers to any user, device, or application that attaches to your network. Without this foundation, you cannot confidently deploy LPA policies and trust that every asset has been classified correctly and received the correct policy. You no longer need one solution for asset discovery and another for deploying and managing policy. Elisity combines this functionality into a single platform, capable of consuming data from a wide variety of sources and integrations that can be used to further enhance the resolution of policies and Policy Groups.
Policy Groups: The Cornerstone of Effective Network Segmentation
The Elisity platform leverages the concept of Policy Groups to automate what was once a manual, tedious task of asset profiling. Rather than individually configuring every asset, or having to reference multiple spreadsheets or CMDBs, Elisity intelligently auto-profiles them as they join the network, subsequently categorizing them into appropriate Policy Groups based on pre-defined match criteria.
Policy Groups are the foundational units for segmentation. Through these, network administrators can establish granular rules and permissions, which are automatically invoked when an asset matches a group's criteria. For instance, Policy Groups could be created for each type of manufacturing equipment, and another set of Policy Groups for the finance department, each with distinct access and usage rights. This enables an unparalleled level of granularity in policy enforcement, freeing up IT staff from routine configuration tasks.

Dynamic Policy Adaptation: The Power of Real-time Responsiveness
Elisity brings unparalleled responsiveness to the complex arena of policy management. As the landscape of your organization shifts—whether through the addition of new network assets or changes in operational requirements—Elisity's platform dynamically matches these assets to the most appropriate Policy Groups based on established criteria, and give you the ability to quickly change policy between various Policy Groups. This automatic reallocation of assets into relevant policy categories not only ensures robust, granular policy enforcement but also aligns with your organization's unique needs and operational tempo. As a result, Elisity elevates both security and operational efficiency, precisely adapting to the ever-changing conditions of your enterprise network.
Orchestrating Policy at Scale: The Versatility and Precision of Policy Sets
Policy Groups are a powerful tool for managing assets on a detailed level, but when you're operating at scale, you need an additional layer that enables a more strategic, organizational-wide approach. That's where Elisity’s Policy Sets come into play. Policy Sets are exactly what they sound like: Sets of Policy Groups that can be applied with a single stroke to different units within your organization—be they sites, departments, or even entire geographic regions.
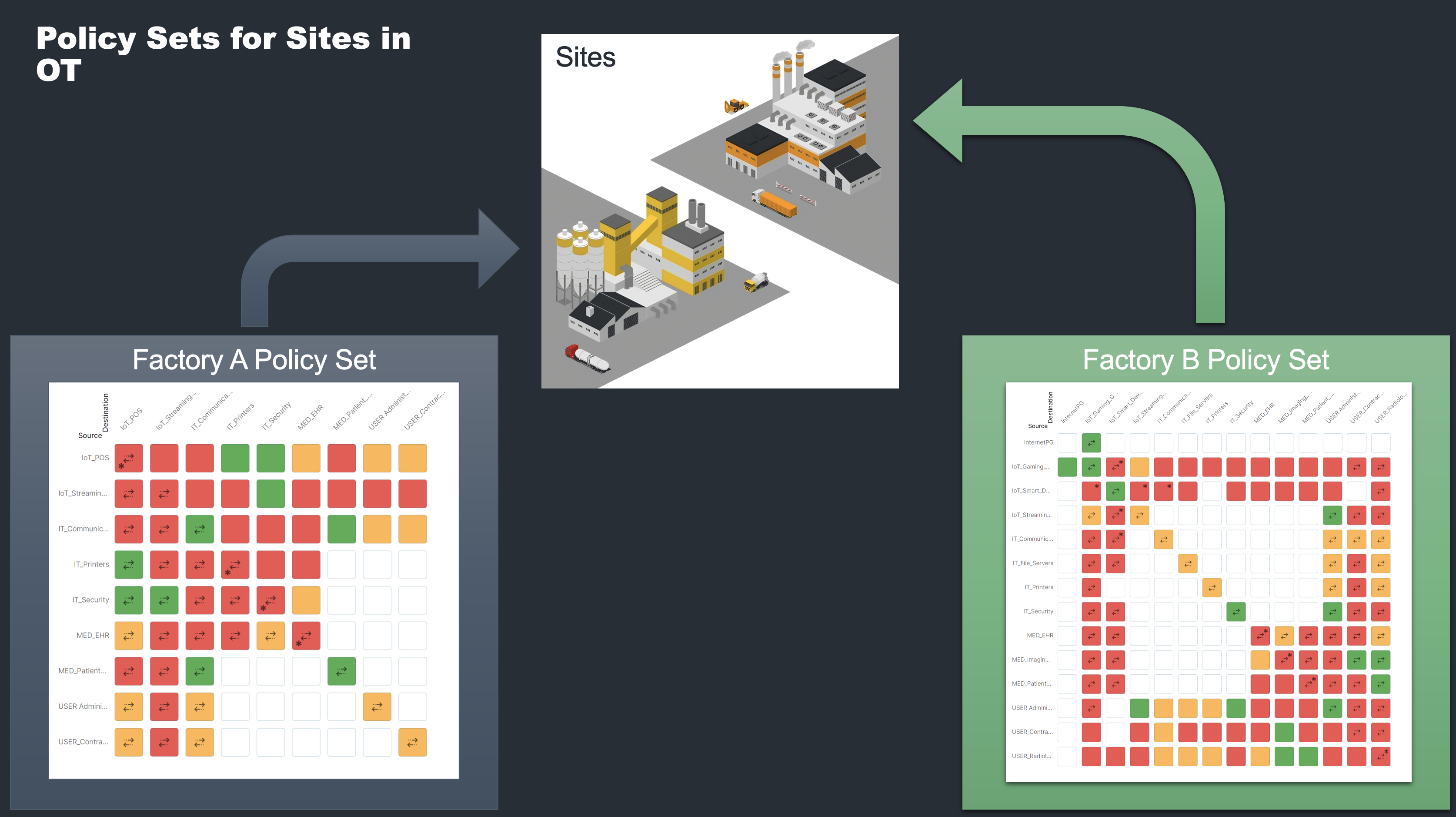
The concept of Policy Sets is transformative in terms of both efficiency and strategic alignment. Consider a multinational corporation that has to abide by GDPR regulations in Europe, HIPAA guidelines in the U.S., or other compliance standard requirements elsewhere. It's true that many of these compliance regulations have overlapping requirements, and they ALL recommend microsegmentation as a solution. However, with Policy Sets, the corporation can create a single GDPR-compliant Policy Set for all its European locations, another HIPAA-aligned set for the U.S., and so on. Perhaps you have two manufacturing facilities that have very different types of machines and processes that have very different network requirements. Policy Sets can be deployed or updated to these sites en masse, which not only saves time but also reduces the risk of error inherent in site-by-site configuration.
Using Policy Sets to Respond to Cybersecurity Events
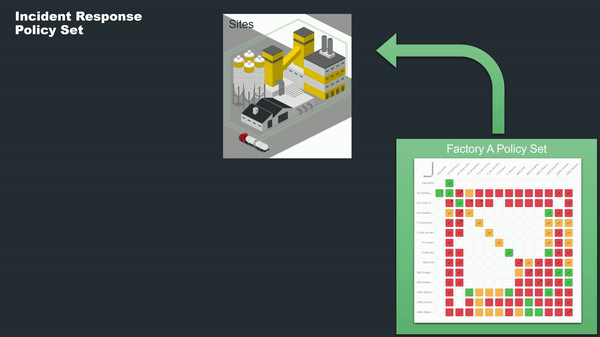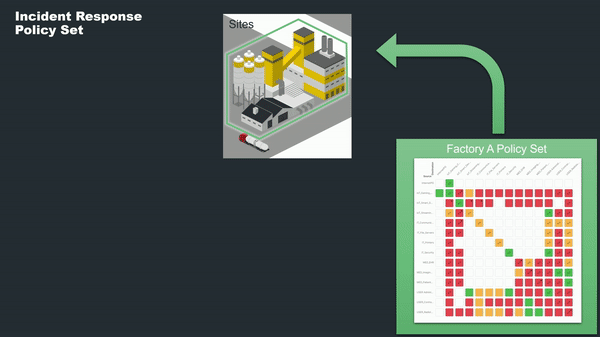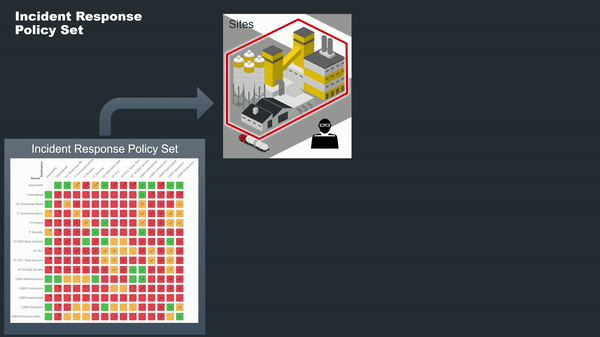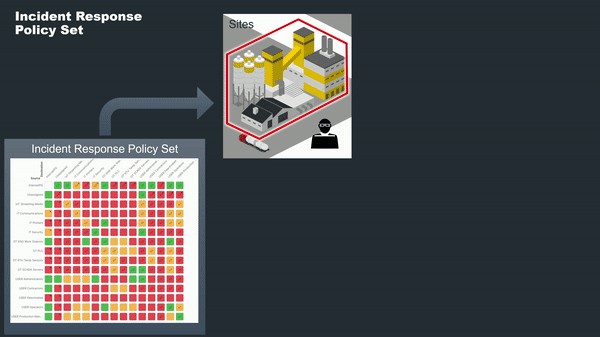
Another incredibly powerful use case offered by Policy Sets is the ability to respond swiftly to unexpected events, like cybersecurity breaches. Elisity enables the creation of specialized "Incident Response Policy Sets," pre-configured to limit network traffic to only the most essential operations. In the event of a detected anomaly or breach, these Policy Sets can be instantaneously applied to the affected sites. This rapid action effectively locks down the network, mitigating risks and containing threats until they can be thoroughly investigated and resolved. The ability to enforce such stringent controls on a site-to-site basis gives organizations the agility to respond to incidents where they occur, without disrupting operations elsewhere.
So, whether you're looking to manage policies across a dispersed organization with diverse regulatory landscapes or need to respond to incidents swiftly and effectively, Elisity's Policy Sets offer a compelling solution. They enable both a high level of customization and rapid action, both of which are invaluable in today's complex and fast-paced business environment.
Reduce Operational Expenses
Elisity dramatically reduces operational costs by simplifying tasks that, in the past, would have consumed a substantial amount of time and resources. Traditional approaches often required organizations to allocate considerable capital in a variety of disparate cybersecurity and network management tools, each with its learning curve and complexities. This not only inflated costs but also necessitated prolonged implementation timelines, creating a slow path to realizing meaningful value. In stark contrast, Elisity's integrated platform offers immediate operational gains right from the onset. By automating processes such as asset profiling and dynamic policy assignment, Elisity eliminates the need for extensive manual intervention, freeing up IT personnel to concentrate on strategic initiatives. This translates into faster time-to-value,
The Transformative Value Proposition of Elisity
Managing the complex landscape of enterprise networks with their ever-growing security demands is a daunting task. Traditional manual methods are increasingly untenable. Elisity bridges this gap by fusing intelligent automation with dynamic, granular policy management. The platform doesn’t merely simplify the lives of IT administrators; it empowers enterprises to navigate safely and efficiently through their complex network landscapes, ensuring they are robustly equipped for present and future challenges.
Share this
- April 2024 (4)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)
No Comments Yet
Let us know what you think