Share this
Understanding the 2021 NSA Zero Trust Guide
by Charlie Treadwell on Mar 16, 2021 6:00:00 AM
On February 25, 2021, the National Security Agency (NSA) published a new document that provides guidance and best practices for organizations working to implement a Zero Trust security strategy. The document explains the Zero Trust model and its many benefits, and recommendations for a successful implementation.
In this blog, we summarize the NSA’s newly released Zero Trust Guide.
Why Zero Trust
The traditional, perimeter-based security strategies that were, or in many cases, still are in place have proven insufficient in several ways. In a traditional environment, the network entry and exit points are guarded by verifying the data packets and identity of users that enter and leave the organization network walls.
This “Castle and Moat” approach revealed several limitations as the threat landscape has advanced so rapidly over recent years. Today, organizations manage networks of apps and data, accessed by employees, customers, and partners onsite or online. This notion makes securing the moat a lot more challenging.
Additionally, in today’s modern enterprises, protecting the perimeter is just the start to an effective security strategy. This technique fails to defend against users with compromised identities or other inside threats that live within perimeter walls as most attacks originate from authorized, but compromised user credentials.
Legacy network security lacks many of the robust security functions needed for adequate protection in the hyper-connected era. This leaves organizations needing to address four areas of focus:
- Coordinated system monitoring, system management, and defensive operations
- Assuming all network traffic may be malicious
- Assuming all devices and infrastructure may be compromised
- Accepting that all access approvals incur risk
The Zero Trust Security Model
According to NSA officials, “The Zero Trust security model eliminates implicit trust in any one element, node, or service and instead requires continuous verification of the operational picture via real-time information fed from multiple sources to determine access and other system responses.”
The NSA Zero Trust Guide articulates that embracing Zero Trust requires operational capabilities that:
- Never trust, always verify: treating every user, device, application/workload, and data flow as untrusted.
- Assume breach: Operate under the assumption that an adversary already has presence within the environment. In other words, deny by default, and heavily scrutinize all users, devices, data flows, and requests for access.
- Verify explicitly: Access should be consistent and secure using multiple attributes (dynamic and static) to derive confidence levels for contextual access decisions to resources.
Additionally, when it comes to designing and implementing a Zero Trust solution, organizations must:
- Define mission outcomes: Architecture should be derived from organizational mission requirements that identify the critical Data/Assets/Applications/Services (DAAS).
- Architect from the inside out: Initially, the focus should be on protecting critical DAAS; Second, all paths to access DAAS should be secured.
- Determine who/what needs access to DAAS to create access control policies: Design security policies that are consistently applied across all environments (LAN, WAN, endpoint, perimeter, mobile, etc.).
- Inspect and log all traffic before acting: Full visibility of all activity across all layers from endpoints and the network need be established to enable analytics so suspicious activity can be detected.
Those looking to implement a Zero Trust architecture must understand and control how users, processes, and devices interact and engage with data.
Zero Trust in Use
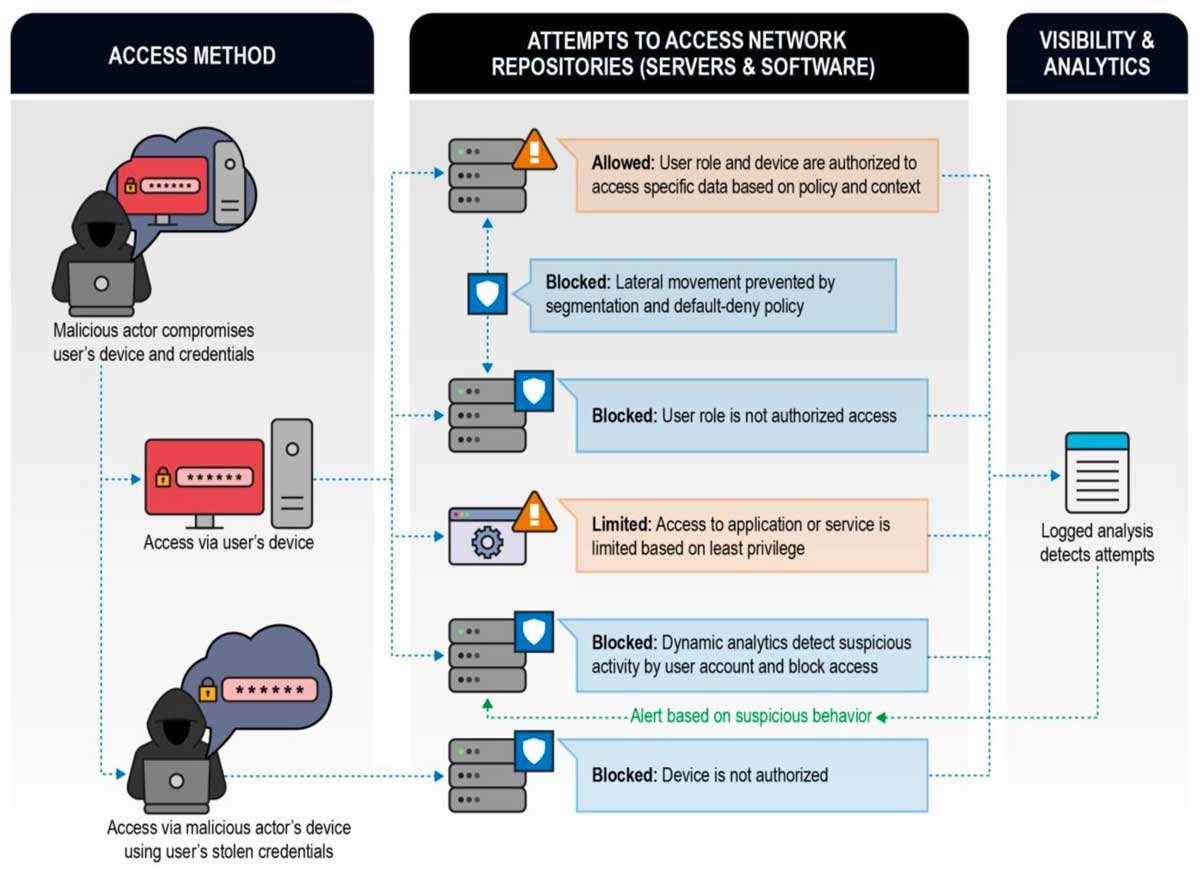
The NSA provides the following example use cases where a Zero Trust implementation works to detect malicious behavior more effectively than a traditional architecture can.
Use Cases
Compromised User Credentials
A malicious cyber-actor compromises a user’s credentials and attempts to access resources. A user’s credentials alone are sufficient to grant access.
With zero trust, when an unauthorized or unknown device attempts access, it fails authentication and is denied, even if that device knows the required login credentials.
Strong authentication is required for user and device identities, and multi-factor authentication is highly recommended, making stealing user credentials more difficult to begin with.
Remote Exploitation or Insider Threat
A malicious actor compromises a user’s device; Or an internal actor with malicious intentions logs onto the network. The malicious actor uses the user’s credentials, enumerates the network, escalates privileges, and moves laterally to compromise data.
With zero trust, real defensive cybersecurity benefits are achieved since the device or application would not be inherently trusted. Its privileges and access to data would be tightly controlled, minimized, and monitored. Segmentation would be enforced by policy and analytics monitor for anomalous activity.
Compromised Supply Chain
A malicious actor embeds malicious code in a popular network device or application. This device or application would be internal, and therefore fully trusted, causing this type of compromise to be particularly severe.
With zero trust, real defensive cybersecurity benefits are achieved since the device or application would not be inherently trusted. Its privileges and access to data would be tightly controlled, minimized, and monitored. Segmentation would be enforced by policy and analytics monitor for anomalous activity.
Implementing Zero Trust can’t be done overnight; it takes time and effort. Assuming existing infrastructure can be leveraged and integrated, the transition to a mature Zero Trust architecture requires additional capabilities to realize the full benefits. The NSA recommends embracing Zero Trust, but that efforts should be planned out as a road-map that continually matures and improves over time.
Potential Challenges on the Path to Zero Trust
Zero Trust Maturity
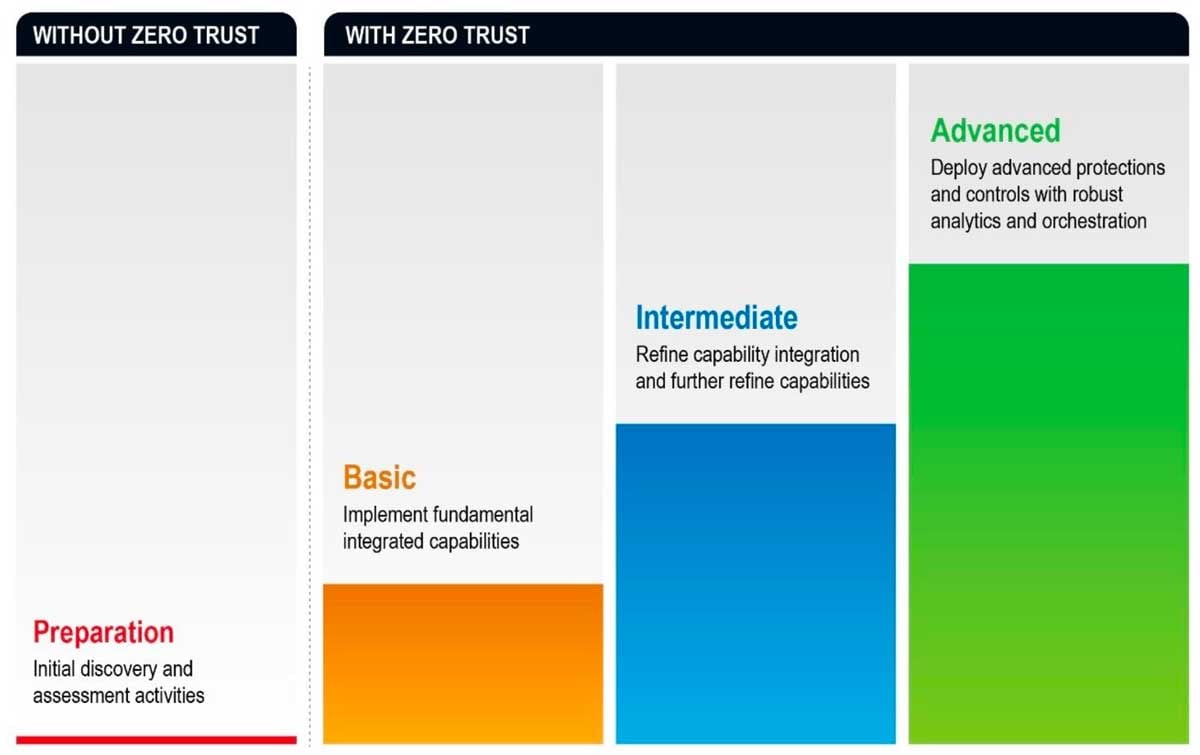
When organizations decide to implement Zero Trust in their network, several challenges may arise that are capable of greatly reducing the effectiveness of the solution.
- Lack of full support throughout the enterprise – Zero Trust must be fully embraced for any solution to be successful, including by users, admins, and executives.
- Lack of scalability of Zero Trust capabilities – Access control is now being performed continuously, as access to the resource is used, requiring a robust infrastructure for making, enforcing, and then logging access decisions.
- Lack of persistent adherence to the Zero Trust mindset and its security model over time – Admins may become fatigued, but if the approach falters, then cybersecurity benefits are degraded or eliminated.
In conclusion, the NSA conveys that with the ever-increasing complexity of network environments and the sophistication of cyber attackers, Zero Trust is needed as a change in defensive focus. The “never trust, always verify” mindset offers security for critical data and access paths, but it’s implementation should not be taken lightly and requires significant resources and persistence to succeed. When properly utilized, Zero Trust can prevent, detect, and contain intrusions significantly faster and more effective than traditional perimeter security approaches.
Share this
- April 2024 (2)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)
No Comments Yet
Let us know what you think